Manage detection rules
editManage detection rules
editThe Rules page allows you to view and manage all prebuilt and custom detection rules.
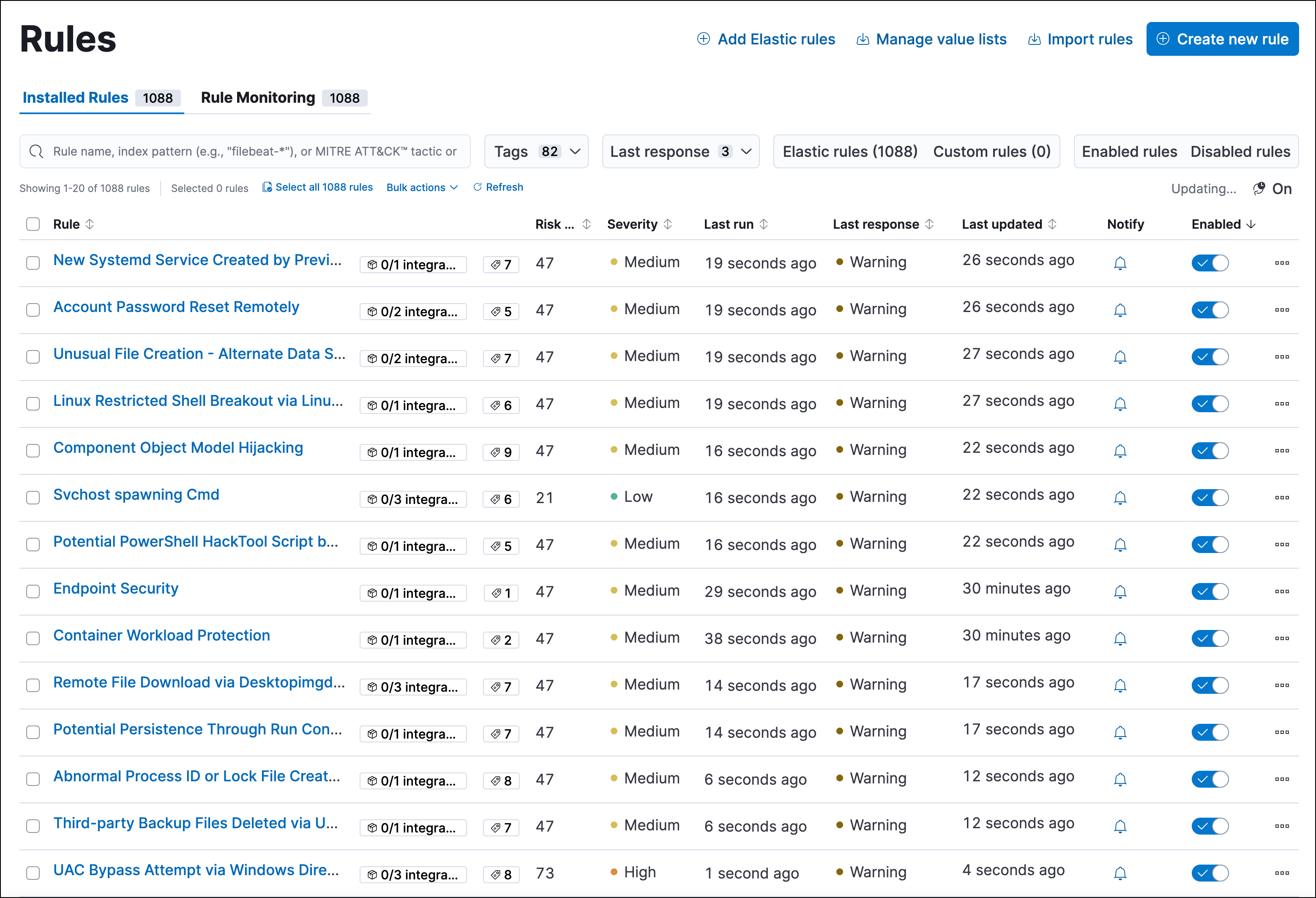
On the Rules page, you can:
Sort and filter the rules list
editTo sort the rules list, click any column header. To sort in descending order, click the column header again.
To filter the rules list, enter a search term in the search bar and press Return:
- Rule name — Enter a word or phrase from a rule’s name.
-
Index pattern — Enter an index pattern (such as
filebeat-*) to display all rules that use it. -
MITRE ATT&CK tactic or technique — Enter a MITRE ATT&CK tactic name (such as
Defense Evasion) or technique number (such asTA0005) to display all associated rules.
Searches for index patterns and MITRE ATT&CK tactics and techniques must match exactly, are case sensitive, and do not support wildcards. For example, to find rules using the filebeat-* index pattern, the search term filebeat-* is valid, but filebeat and file* are not because they don’t exactly match the index pattern. Likewise, the MITRE ATT&CK tactic Defense Evasion is valid, but Defense, defense evasion, and Defense* are not.
You can also filter the rules list by selecting the Tags, Last response, Elastic rules, Custom rules, Enabled rules, and Disabled rules filters next to the search bar.
The rules list retains your sorting and filtering settings when you navigate away and return to the page. These settings are also preserved when you copy the page’s URL and paste into another browser. Select Clear filters above the table to revert to the default view.
Check the current status of rules
editThe Last response column displays the current status of each rule, based on the most recent attempt to run the rule:
- Succeeded: The rule completed its defined search. This doesn’t necessarily mean it generated an alert, just that it ran without error.
- Failed: The rule encountered an error that prevented it from running. For example, a machine learning rule whose corresponding machine learning job wasn’t running.
- Warning: Nothing prevented the rule from running, but it might have returned unexpected results. For example, a custom query rule tried to search an index pattern that couldn’t be found in Elasticsearch.
For machine learning rules, an indicator icon (![]() ) also appears in this column if a required machine learning job isn’t running. Click the icon to list the affected jobs, then click Visit rule details page to investigate to open the rule’s details page, where you can start the machine learning job.
) also appears in this column if a required machine learning job isn’t running. Click the icon to list the affected jobs, then click Visit rule details page to investigate to open the rule’s details page, where you can start the machine learning job.
Modify existing rules settings
editYou can edit an existing rule’s settings, and can bulk edit settings for multiple rules at once.
For prebuilt Elastic rules, you can’t modify most settings. You can only edit rule actions and add exceptions. If you try to bulk edit with both prebuilt and custom rules selected, the action will affect only the rules that can be modified.
Similarly, rules will be skipped if they can’t be modified by a bulk edit. For example, if you try to apply a tag to rules that already have that tag, or apply an index pattern to rules that use data views.
- Find Detection rules (SIEM) in the navigation menu or by using the global search field.
-
Do one of the following:
- Edit a single rule: Select the All actions menu (…) on a rule, then select Edit rule settings. The Edit rule settings view opens, where you can modify the rule’s settings.
-
Bulk edit multiple rules: Select the rules you want to edit, then select an action from the Bulk actions menu:
- Index patterns: Add or delete the index patterns used by all selected rules.
- Tags: Add or delete tags on all selected rules.
- Custom highlighted fields: Add custom highlighted fields on all selected rules. You can choose any fields that are available in the default Elastic Security indices, or enter field names from other indices. To overwrite a rule’s current set of custom highlighted fields, select the Overwrite all selected rules' custom highlighted fields option, then click Save.
- Add rule actions: Add rule actions on all selected rules. If you add multiple actions, you can specify an action frequency for each of them. To overwrite the frequency of existing actions select the option to Overwrite all selected rules actions.
After upgrading to 8.8 or later, frequency settings for rule actions created in 8.7 or earlier are moved from the rule level to the action level. The action schedules remain the same and will continue to run on their previously specified frequency (
On each rule execution,Hourly,Daily, orWeekly).
Rule actions won’t run during a maintenance window. They’ll resume running after the maintenance window ends.
- Update rule schedules: Update the schedules and look-back times on all selected rules.
- Apply Timeline template: Apply a specified Timeline template to the selected rules. You can also choose None to remove Timeline templates from the selected rules.
-
On the flyout that opens, update the rule settings and actions.
To snooze rule actions, go to the Actions tab and click the bell icon.
- If available, select Overwrite all selected x to overwrite the settings on the rules. For example, if you’re adding tags to multiple rules, selecting Overwrite all selected rules tags removes all the rules' original tags and replaces them with the tags you specify.
- Click Save.
Manage rules
editYou can duplicate, enable, disable, delete, and snooze actions for rules:
When duplicating a rule with exceptions, you can choose to duplicate the rule and its exceptions (active and expired), the rule and active exceptions only, or only the rule. If you duplicate the rule and its exceptions, copies of the exceptions are created and added to the duplicated rule’s default rule list. If the original rule used exceptions from a shared exception list, the duplicated rule will reference the same shared exception list.
- Find Detection rules (SIEM) in the navigation menu or by using the global search field.
-
In the Rules table, do one of the following:
- Select the All actions menu (…) on a rule, then select an action.
- Select all the rules you want to modify, then select an action from the Bulk actions menu.
- To enable or disable a single rule, switch on the rule’s Enabled toggle.
- To snooze actions for rules, click the bell icon.
Run rules manually
editThis functionality is in beta and is subject to change. The design and code is less mature than official GA features and is being provided as-is with no warranties. Beta features are not subject to the support SLA of official GA features.
Manually run enabled rules for a specified period of time for testing purposes or additional rule coverage.
Before manually running rules, make sure you properly understand and plan for rule dependencies. Incorrect scheduling can lead to inconsistent rule results.
- Find Detection rules (SIEM) in the navigation menu or by using the global search field.
-
In the Rules table, do one of the following:
- Select the All actions menu (…) on a rule, then select Manual run.
- Select all the rules you want to manually run, select the Bulk actions menu, then select Manual run.
- Specify when the manual run starts and ends. The default selection is the current day starting three hours in the past. The rule will search for events during the selected time range.
-
Click Run to manually run the rule.
Manual runs can produce multiple rule executions. This is determined by the manual run’s time range and the rule’s execution schedule.
The manual run’s details are shown in the Manual runs table on the Execution results tab. Changes you make to the manual run or rule settings will display in the Manual runs table after the current run completes.
Be mindful of the following:
- Rule actions are not activated during manual runs.
- Except for threshold rules, duplicate alerts aren’t created if you manually run a rule during a time range that was already covered by a scheduled run.
- Manual runs are executed with low priority and limited concurrency, meaning they might take longer to complete. This can be especially apparent for rules requiring multiple executions.
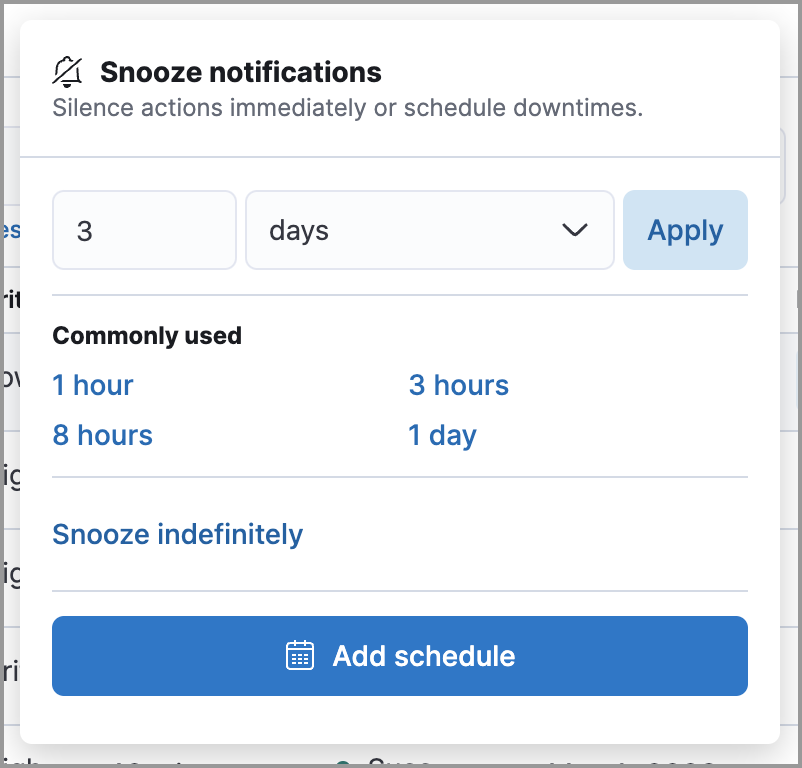
Snooze rule actions
editInstead of turning rules off to stop alert notifications, you can snooze rule actions for a specified time period. When you snooze rule actions, the rule continues to run on its defined schedule, but won’t perform any actions or send alert notifications.
You can snooze notifications temporarily or indefinitely. When actions are snoozed, you can cancel or change the duration of the snoozed state. You can also schedule and manage recurring downtime for actions.
You can snooze rule notifications from the Installed Rules tab, the rule details page, or the Actions tab when editing a rule.
Export and import rules
editYou can export custom detection rules to an .ndjson file, which you can then import into another Elastic Security environment.
You cannot export Elastic prebuilt rules, but you can duplicate a prebuilt rule, then export the duplicated rule.
If you try to export with both prebuilt and custom rules selected, only the custom rules are exported.
The .ndjson file also includes any actions, connectors, and exception lists related to the exported rules. However, other configuration items require additional handling when exporting and importing rules:
-
Data views: For rules that use a Kibana data view as a data source, the exported file contains the associated
data_view_id, but does not include any other data view configuration. To export/import between Kibana spaces, first use the Saved Objects UI to share the data view with the destination space.To import into a different Elastic Stack deployment, the destination cluster must include a data view with a matching data view ID (configured in the data view’s advanced settings). Alternatively, after importing, you can manually reconfigure the rule to use an appropriate data view in the destination system.
-
Actions and connectors: Rule actions and connectors are included in the exported file, but sensitive information about the connector (such as authentication credentials) is not included. You must re-add missing connector details after importing detection rules.
You can also use Kibana’s Saved Objects UI to export and import necessary connectors before importing detection rules.
- Value lists: Any value lists used for rule exceptions are not included in rule exports or imports. Use the Manage value lists UI to export and import value lists separately.
To export and import detection rules:
- Find Detection rules (SIEM) in the navigation menu or by using the global search field.
-
To export rules:
- In the Rules table, select the rules you want to export.
- Select Bulk actions → Export, then save the exported file.
-
To import rules:
To import rules with actions, you need at least
Readprivileges for theAction and Connectorsfeature. To overwrite or add new connectors, you needAllprivileges for theActions and Connectorsfeature. To import rules without actions, you don’t needActions and Connectorsprivileges. Refer to Enable and access detections for more information.- Click Import rules.
-
Drag and drop the file that contains the detection rules.
Imported rules must be in an
.ndjsonfile. -
(Optional) Select Overwrite existing detection rules with conflicting "rule_id" to update existing rules if they match the
rule_idvalue of any rules in the import file. Configuration data included with the rules, such as actions, is also overwritten. -
(Optional) Select Overwrite existing exception lists with conflicting "list_id" to replace existing exception lists with exception lists from the import file if they have a matching
list_idvalue. -
(Optional) Select Overwrite existing connectors with conflicting action "id" to update existing connectors if they match the
action idvalue of any rule actions in the import file. Configuration data included with the actions is also overwritten. - Click Import rule.
- (Optional) If a connector is missing sensitive information after the import, a warning displays and you’re prompted to fix the connector. In the warning, click Go to connector. On the Connectors page, find the connector that needs to be updated, click Fix, then add the necessary details.
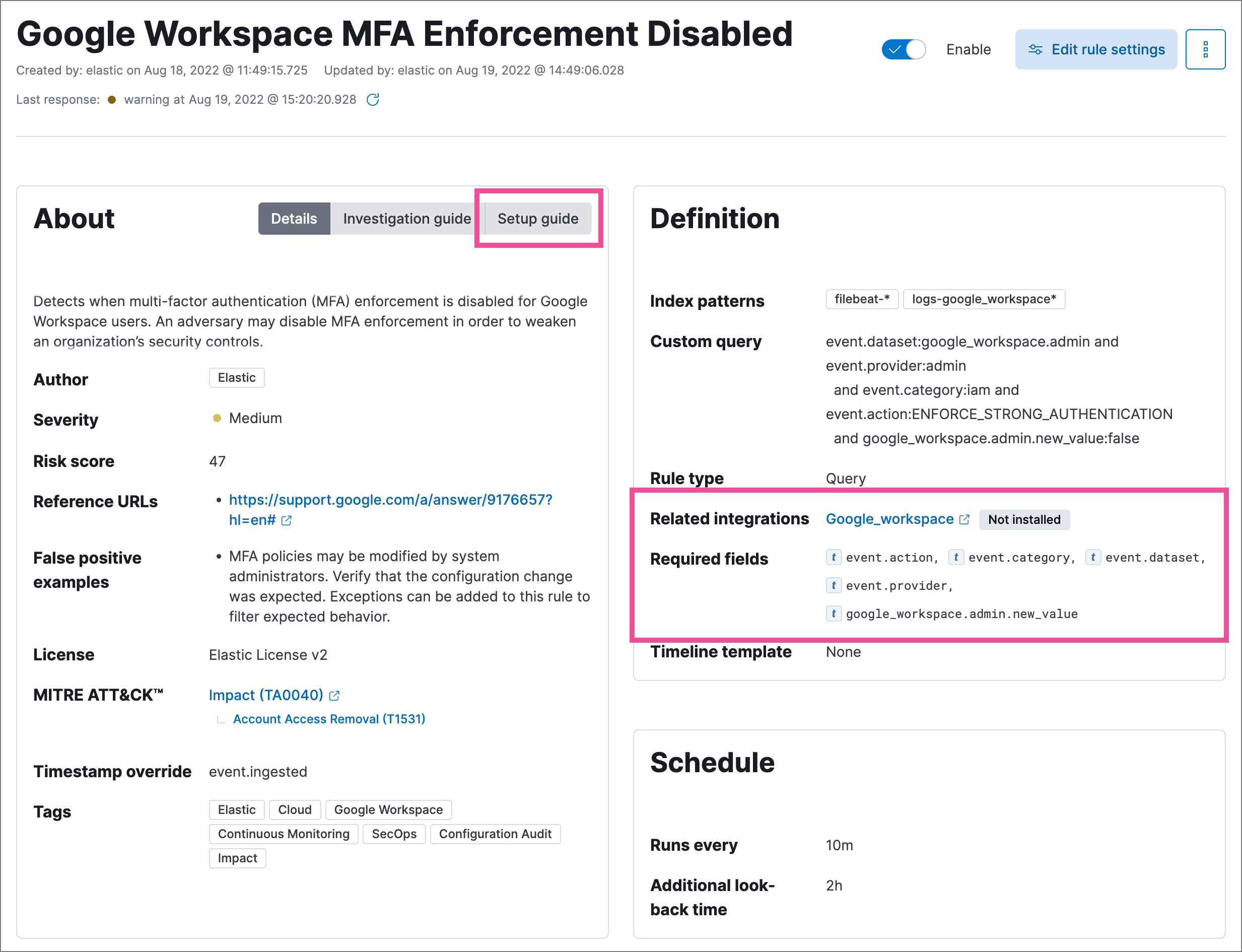
Confirm rule prerequisites
editMany detection rules are designed to work with specific Elastic integrations and data fields. These prerequisites are identified in Related integrations and Required fields on a rule’s details page. Related integrations also displays each integration’s installation status and includes links for installing and configuring the listed integrations.
Additionally, the Setup guide section provides guidance on setting up the rule’s requirements.
You can also check rules' related integrations in the Installed Rules and Rule Monitoring tables. Click the integrations badge to display the related integrations in a popup.
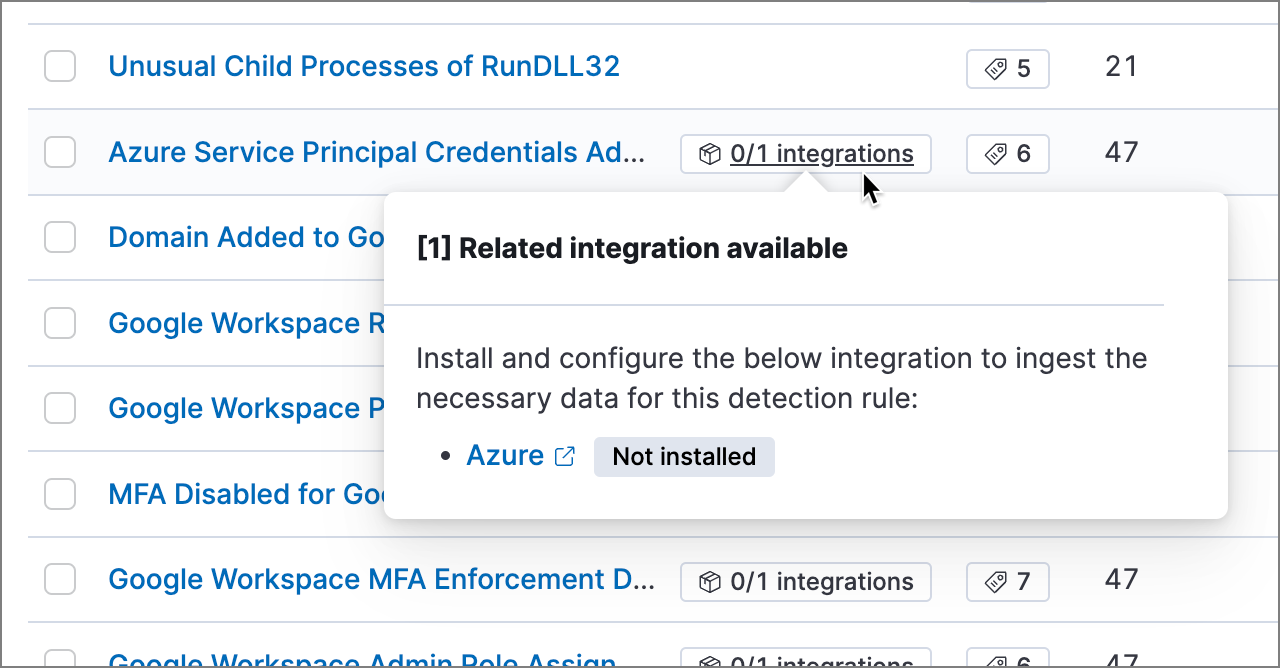
You can hide the integrations badge in the rules tables. To do this, turn off securitySolution:showRelatedIntegrations advanced setting.