- Fleet and Elastic Agent Guide: other versions:
- Fleet and Elastic Agent overview
- Beats and Elastic Agent capabilities
- Quick starts
- Migrate from Beats to Elastic Agent
- Deployment models
- Install Elastic Agents
- Install Fleet-managed Elastic Agents
- Install standalone Elastic Agents
- Install Elastic Agents in a containerized environment
- Run Elastic Agent in a container
- Run Elastic Agent on Kubernetes managed by Fleet
- Install Elastic Agent on Kubernetes using Helm
- Example: Install standalone Elastic Agent on Kubernetes using Helm
- Example: Install Fleet-managed Elastic Agent on Kubernetes using Helm
- Advanced Elastic Agent configuration managed by Fleet
- Configuring Kubernetes metadata enrichment on Elastic Agent
- Run Elastic Agent on GKE managed by Fleet
- Run Elastic Agent on Amazon EKS managed by Fleet
- Run Elastic Agent on Azure AKS managed by Fleet
- Run Elastic Agent Standalone on Kubernetes
- Scaling Elastic Agent on Kubernetes
- Using a custom ingest pipeline with the Kubernetes Integration
- Environment variables
- Run Elastic Agent as an OTel Collector
- Run Elastic Agent without administrative privileges
- Install Elastic Agent from an MSI package
- Installation layout
- Air-gapped environments
- Using a proxy server with Elastic Agent and Fleet
- Uninstall Elastic Agents from edge hosts
- Start and stop Elastic Agents on edge hosts
- Elastic Agent configuration encryption
- Secure connections
- Manage Elastic Agents in Fleet
- Configure standalone Elastic Agents
- Create a standalone Elastic Agent policy
- Structure of a config file
- Inputs
- Providers
- Outputs
- SSL/TLS
- Logging
- Feature flags
- Agent download
- Config file examples
- Grant standalone Elastic Agents access to Elasticsearch
- Example: Use standalone Elastic Agent with Elastic Cloud Serverless to monitor nginx
- Example: Use standalone Elastic Agent with Elasticsearch Service to monitor nginx
- Debug standalone Elastic Agents
- Kubernetes autodiscovery with Elastic Agent
- Monitoring
- Reference YAML
- Manage integrations
- Package signatures
- Add an integration to an Elastic Agent policy
- View integration policies
- Edit or delete an integration policy
- Install and uninstall integration assets
- View integration assets
- Set integration-level outputs
- Upgrade an integration
- Managed integrations content
- Best practices for integration assets
- Data streams
- Define processors
- Processor syntax
- add_cloud_metadata
- add_cloudfoundry_metadata
- add_docker_metadata
- add_fields
- add_host_metadata
- add_id
- add_kubernetes_metadata
- add_labels
- add_locale
- add_network_direction
- add_nomad_metadata
- add_observer_metadata
- add_process_metadata
- add_tags
- community_id
- convert
- copy_fields
- decode_base64_field
- decode_cef
- decode_csv_fields
- decode_duration
- decode_json_fields
- decode_xml
- decode_xml_wineventlog
- decompress_gzip_field
- detect_mime_type
- dissect
- dns
- drop_event
- drop_fields
- extract_array
- fingerprint
- include_fields
- move_fields
- parse_aws_vpc_flow_log
- rate_limit
- registered_domain
- rename
- replace
- script
- syslog
- timestamp
- translate_sid
- truncate_fields
- urldecode
- Command reference
- Troubleshoot
- Release notes
One-way and mutual TLS certifications flow
editOne-way and mutual TLS certifications flow
editThis page provides an overview of the relationship between the various certificates and certificate authorities (CAs) that you configure for Fleet Server and Elastic Agent, using the elastic-agent install TLS command options.
Simple one-way TLS connection
editThe following elastic-agent install command configures a Fleet Server with the required certificates and certificate authorities to enable one-way TLS connections between the components involved:
elastic-agent install --url=https://your-fleet-server.elastic.co:443 \ --certificate-authorities=/path/to/fleet-ca \ --fleet-server-es=https://es.elastic.com:443 \ --fleet-server-es-ca=/path/to/es-ca \ --fleet-server-cert=/path/to/fleet-cert \ --fleet-server-cert-key=/path/to/fleet-cert-key \ --fleet-server-service-token=FLEET-SERVER-SERVICE-TOKEN \ --fleet-server-policy=FLEET-SERVER-POLICY-ID \ --fleet-server-port=8220
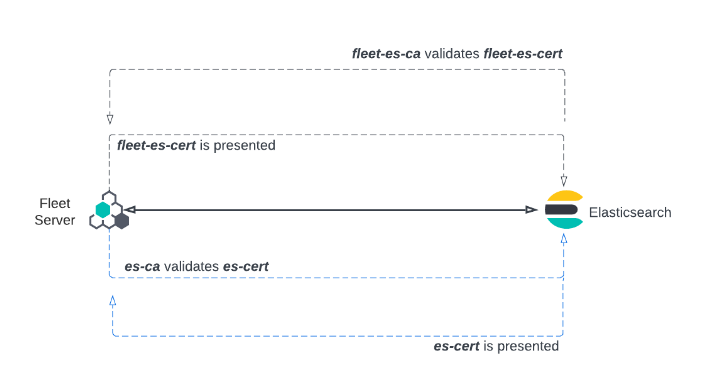
Elastic Agent is configured with fleet-ca as the certificate authority that it needs to validate certificates from Fleet Server.
During the TLS connection setup, Fleet Server presents its certificate fleet-cert to the agent and the agent (as a client) uses fleet-ca to validate the presented certificate.
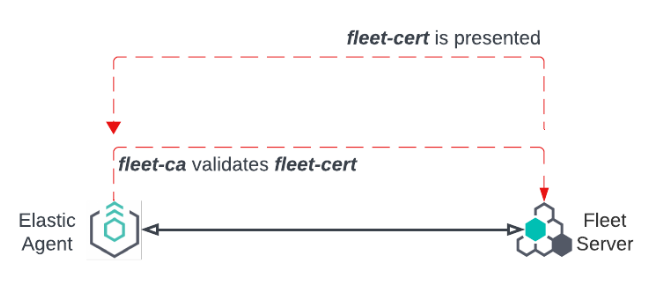
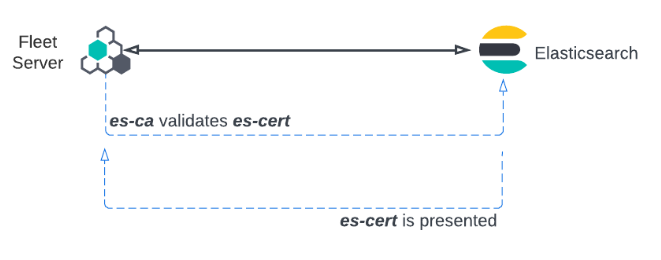
Fleet Server also establishes a secure connection to an Elasticsearch cluster. In this case, Fleet Server is configured with the certificate authority from the Elasticsearch es-ca. Elasticsearch presents its certificate, es-cert, and Fleet Server validates the presented certificate using the certificate authority es-ca.
Relationship between components in a one-way TLS connection
edit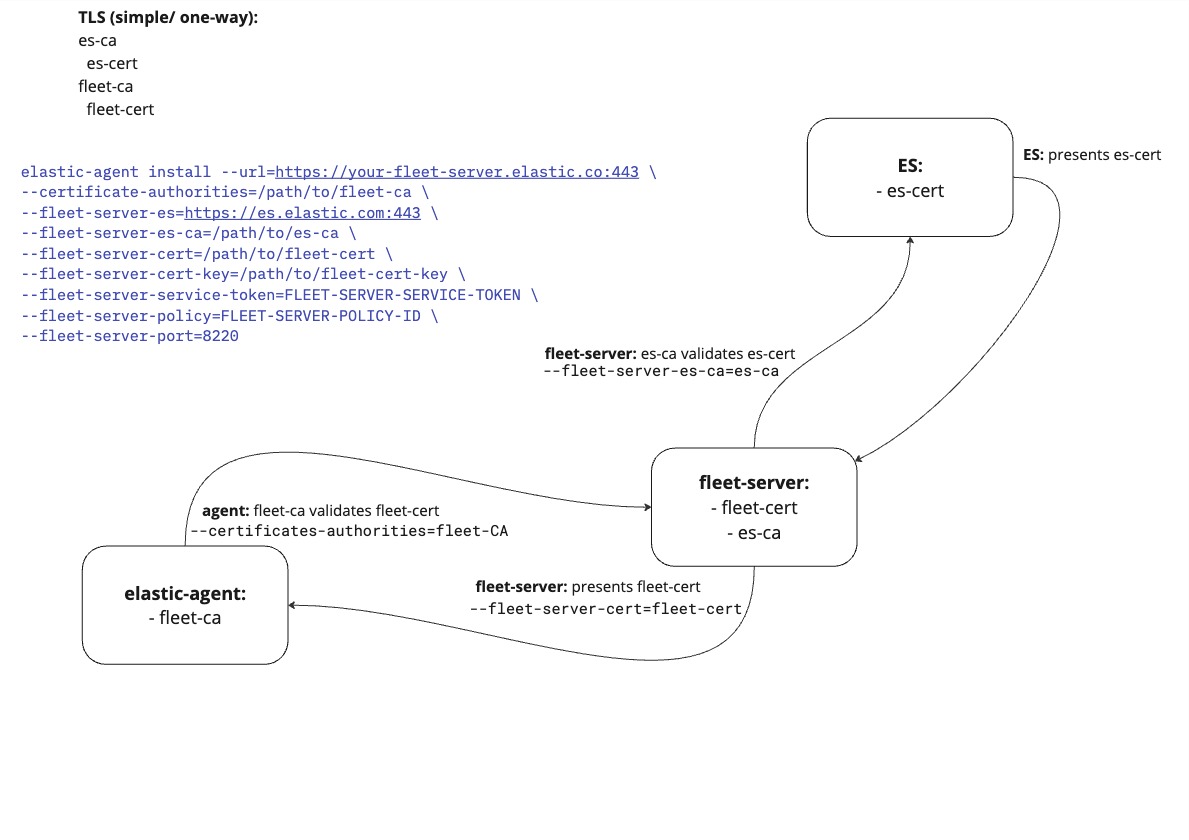
Mutual TLS connection
editThe following elastic-agent install command configures a Fleet Server with the required certificates and certificate authorities to enable mutual TLS connections between the components involved:
elastic-agent install --url=https://your-fleet-server.elastic.co:443 \ --certificate-authorities=/path/to/fleet-ca,/path/to/agent-ca \ --elastic-agent-cert=/path/to/agent-cert \ --elastic-agent-cert-key=/path/to/agent-cert-key \ --elastic-agent-cert-key=/path/to/agent-cert-key-passphrase \ --fleet-server-es=https://es.elastic.com:443 \ --fleet-server-es-ca=/path/to/es-ca \ --fleet-server-es-cert=/path/to/fleet-es-cert \ --fleet-server-es-cert-key=/path/to/fleet-es-cert-key \ --fleet-server-cert=/path/to/fleet-cert \ --fleet-server-cert-key=/path/to/fleet-cert-key \ --fleet-server-client-auth=required \ --fleet-server-service-token=FLEET-SERVER-SERVICE-TOKEN \ --fleet-server-policy=FLEET-SERVER-POLICY-ID \ --fleet-server-port=8220
As with the one-way TLS example, Elastic Agent is configured with fleet-ca as the certificate authority that it needs to validate certificates from the Fleet Server. Fleet Server presents its certificate fleet-cert to the agent and the agent (as a client) uses fleet-ca to validate the presented certificate.
To establish a mutual TLS connection, the agent presents its certificate, agent-cert, and Fleet Server validates this certificate using the agent-ca that it has stored in memory.
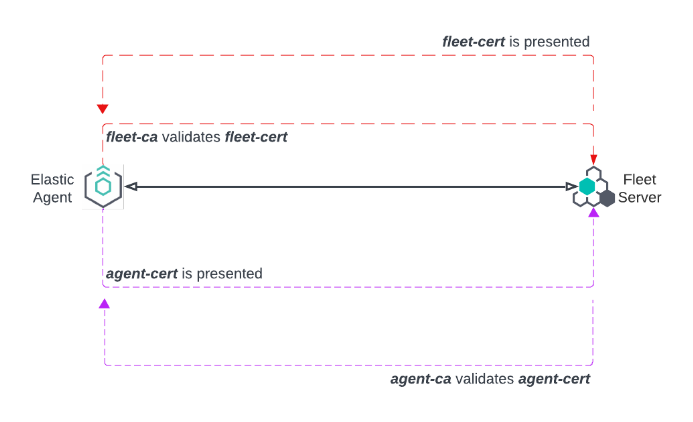
Fleet Server can also establish a mutual TLS connection to the Elasticsearch cluster. In this case, Fleet Server is configured with the certificate authority from the Elasticsearch es-ca and uses this to validate the certificate es-cert presented to it by Elasticsearch.
Note that you can also configure mutual TLS for Fleet Server and Elastic Agent using a proxy.
Relationship between components in a mutual TLS connection
edit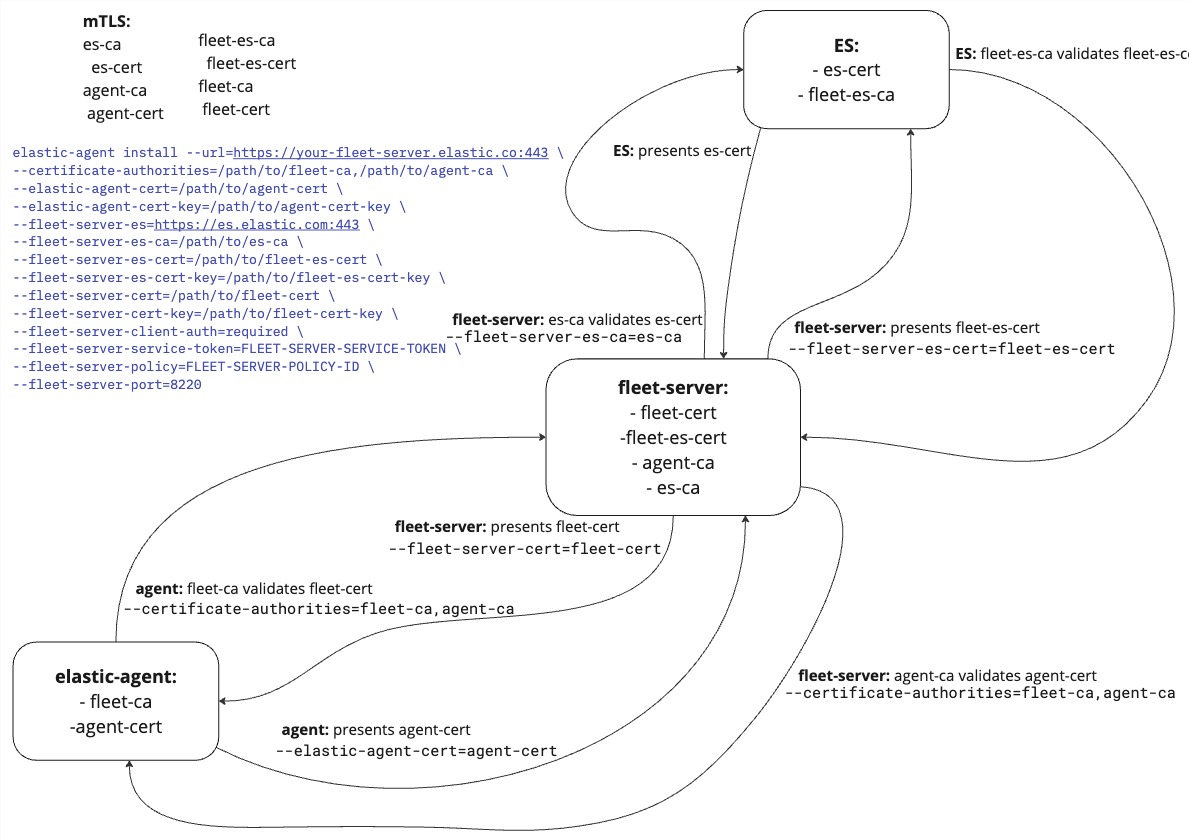
On this page