It is time to say goodbye: This version of Elastic Cloud Enterprise has reached end-of-life (EOL) and is no longer supported.
The documentation for this version is no longer being maintained. If you are running this version, we strongly advise you to upgrade. For the latest information, see the current release documentation.
Networking prerequisites
editNetworking prerequisites
editThe first host you install ECE on initially requires the ports for all roles to be open, which includes the ports for the coordinator, allocator, director, and proxy roles. After you have brought up your initial ECE installation, only the ports for the roles that the initial host continues to hold need to remain open. Before installing a runner, make sure that the 20000, 21000, 22000 ports are open for the installation script checks.
For versions 2.4.0 and 2.4.1, IPv6 should remain enabled on any host with the Proxy role. In 2.4.2 and later, IPv6 can be disabled.
Inbound traffic
editWhen there are multiple hosts for each role, the inbound networking and ports can be represented by the following diagram:
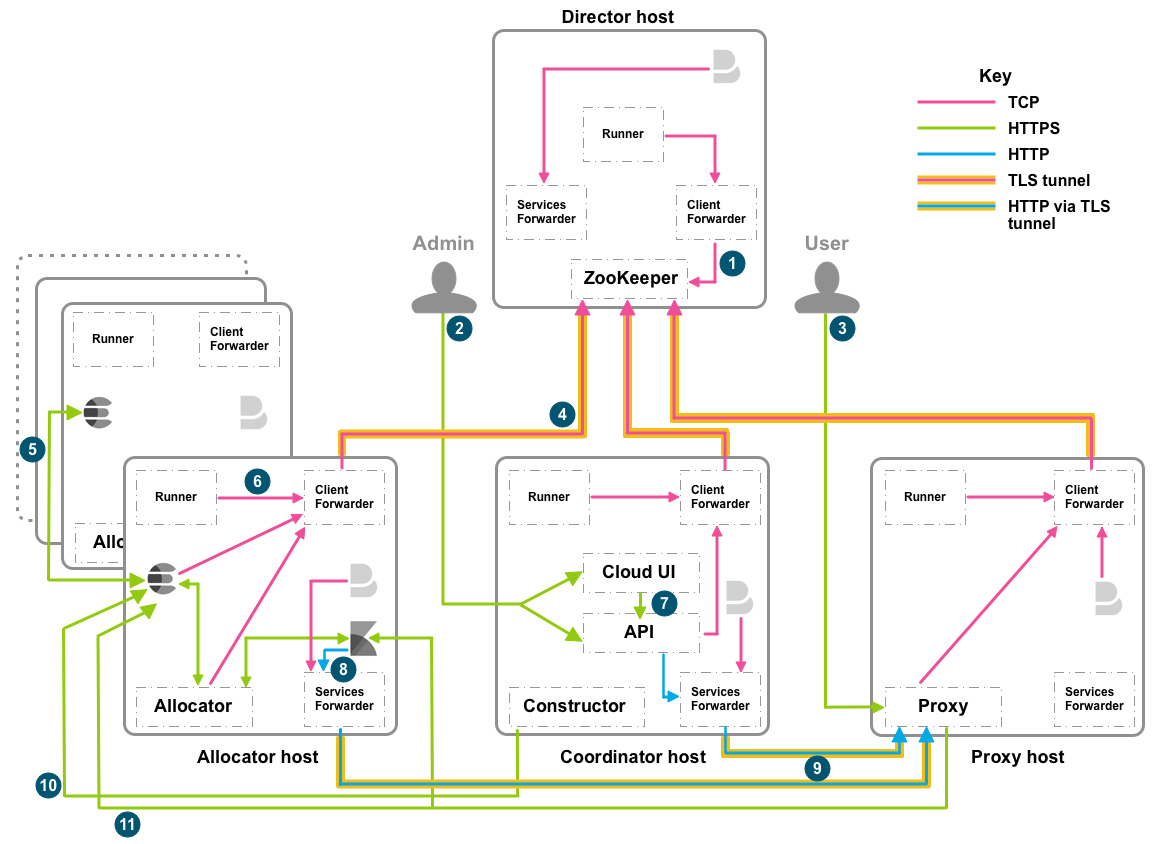
Inbound traffic from any source
| Number | Host role | Inbound ports | *Purpose* |
|---|---|---|---|
All |
22 |
Installation and troubleshooting SSH access only (TCP) |
|
2 |
Coordinator |
12300/12343, 12400/12443 |
Admin API access (HTTP/HTTPS) |
3 |
Proxy |
9200/9243, 9300/9343 |
Elasticsearch (transport client/transport client with TLS/SSL), also required by load balancers |
7 |
Coordinator |
12400/12443 |
Cloud UI console to API (HTTP/HTTPS) |
Inbound traffic from internal components of ECE
In addition to the following list, you should open 12898-12908 and 13898-13908 on the director host for Zookeeper leader and election activity.
| Number | Host role | Inbound ports | *Purpose* |
|---|---|---|---|
1 |
Director |
2112 |
ZooKeeper ensemble discovery/joining (TCP) |
4 |
Director |
12191-12201 |
Client forwarder to ZooKeeper, one port per director (TLS tunnels) |
5 |
Allocator |
19000-19999 |
Elasticsearch node to node (Node Transport 6.x+/TLS 6.x+) |
6 |
Allocator |
18000-18999/20000-20999 |
Proxy to Elasticsearch/Kibana/APM Server instance (HTTPS/Transport Client 6.x+/TLS 6.x+) |
7 |
Coordinator |
22191-22195 |
Connections to initial coordinator from allocators and proxies, one port per coordinator, up to five (TCP) |
8 |
Allocator |
9244 |
Kibana to the services forwarder (HTTP) |
9 |
Proxy |
9200/9243, 9300/9343 |
Kibana and Elasticsearch (HTTP via TLS tunnel) |
10 |
Allocator |
18000-18999 |
Constructor to Elasticsearch cluster (HTTPS) |
11 |
Allocator |
18000-18999/20000-20999 |
Elasticsearch (HTTPS/Transport Client TLS) |
12 |
Allocator |
21000-21999 |
APM Server (Instance Monitoring) |
13 |
Proxy |
9000/9043 |
Proxy metrics endpoint (HTTP/HTTPS) |
Outbound traffic
editOpen these ports for outbound traffic:
| Host role | Outbound ports | Purpose |
|---|---|---|
All |
80 |
Installation script and docker.elastic.co Docker registry access (HTTP) |
All |
443 |
Installation script and docker.elastic.co Docker registry access (HTTPS) |
Hosts in multiple data centers
editA typical ECE installation should be contained within a single data center. We recommend that ECE installations not span different data centers, due to variations in networking latency and bandwidth that cannot be controlled.
Installation of ECE across multiple data centers might be feasible with sufficiently low latency and high bandwidth, with some restrictions around what we can support. Based on our experience with our hosted Elastic Cloud service, the following is required:
- A typical network latency between the data centers of less than 10ms round-trip time during pings
- A network bandwidth of at least 10 Gigabit
If you choose to deploy a single ECE installation across multiple data centers, you might need to contend with additional disruptions due to bandwidth or latency issues. Both ECE and Elasticsearch are designed to be resilient to networking issues, but this resiliency is intended to handle exceptions and should not be depended on as part of normal operations. If Elastic determines during a support case that an issue is related to an installation across multiple data centers, the recommended resolution will be to consolidate your installation into a single data center, with further support limited until consolidation is complete.