Connecting SharePoint Online
editConnecting SharePoint Online
editSharePoint Online by Microsoft is a cloud-based collaboration, knowledge management and storage platform for organizations of all sizes. Often used as a centralized content management system (CMS), SharePoint Online stores a wealth of information across departments and teams. The SharePoint Online connector provided with Workplace Search automatically captures, syncs and indexes the following items:
Stored Files |
Including ID, File Metadata, File Content, Updated by, and timestamps |
Known issues
edit-
When configured after November 8, 2020, the SharePoint Online connector must be connected by an Azure AD admin user. Therefore, private sources are not supported. Organization sources are supported when connected by an Azure AD admin user.
During configuration, you register an OAuth app in Azure AD that does not have a verified publisher. After November 8, 2020, these apps can be connected by Azure AD admin users only.
Configuring the SharePoint Online Connector
editConfiguring the SharePoint Online connector is the first step prior to connecting the SharePoint Online service to Workplace Search, and requires that you create an OAuth App from the SharePoint Online platform. To get started, first log in to SharePoint Online and access your administrative dashboard:
Step 1. Sign in to https://portal.azure.com/ and click on Azure Active Directory:
Step 2. Locate App Registrations:
Step 3. Click New Registration:
Step 4. Give your app a name - like "Workplace Search" - and make it multitenant.
Setting the app to single tenant will result in a degraded experience, and the connector will not sync content.
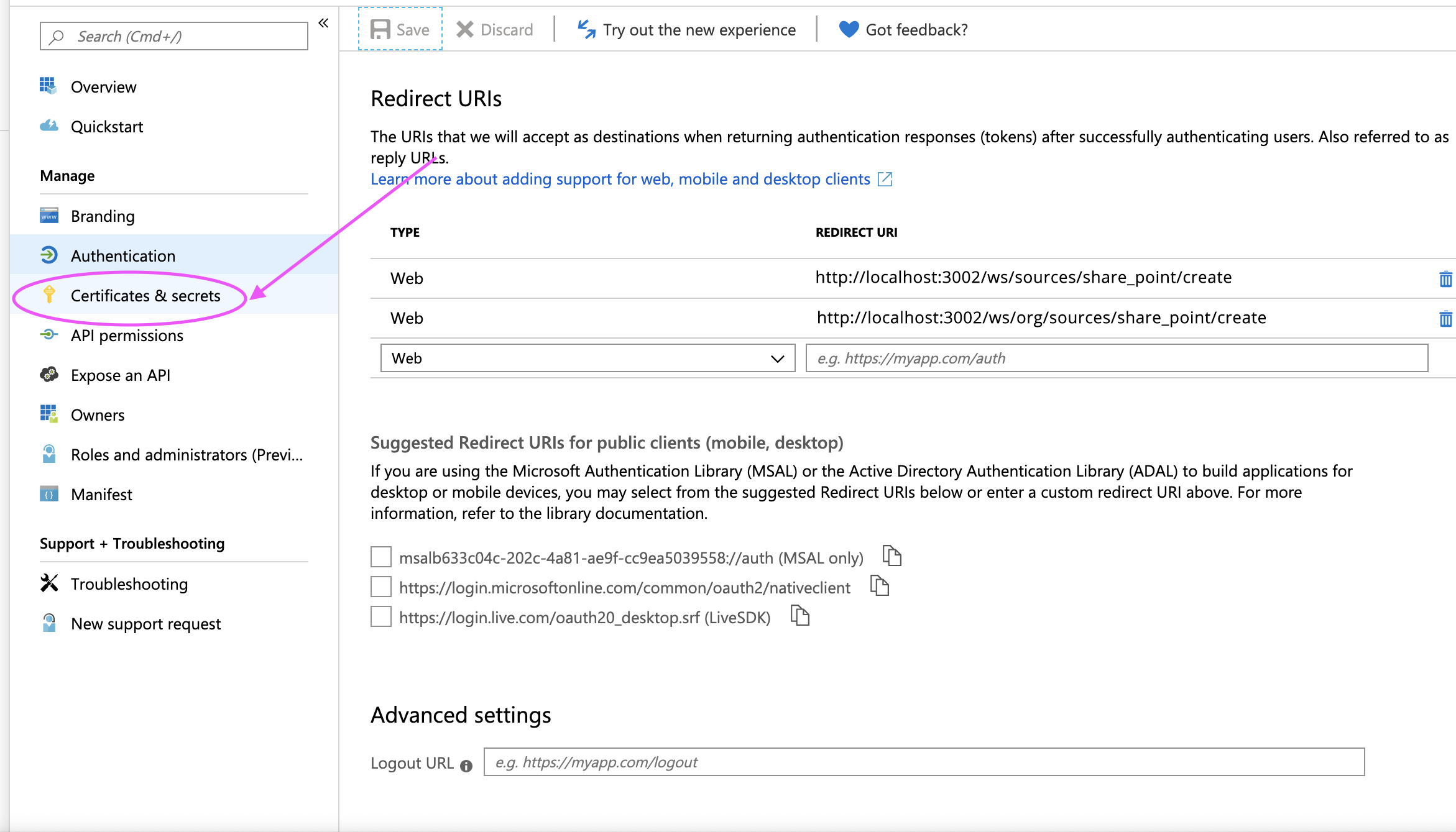
Leave the Redirect URIs blank for now. We will need two: one for Organizational Sources and the other for Personal Sources. We’ll add this later in the process.
Step 5. Register the application:
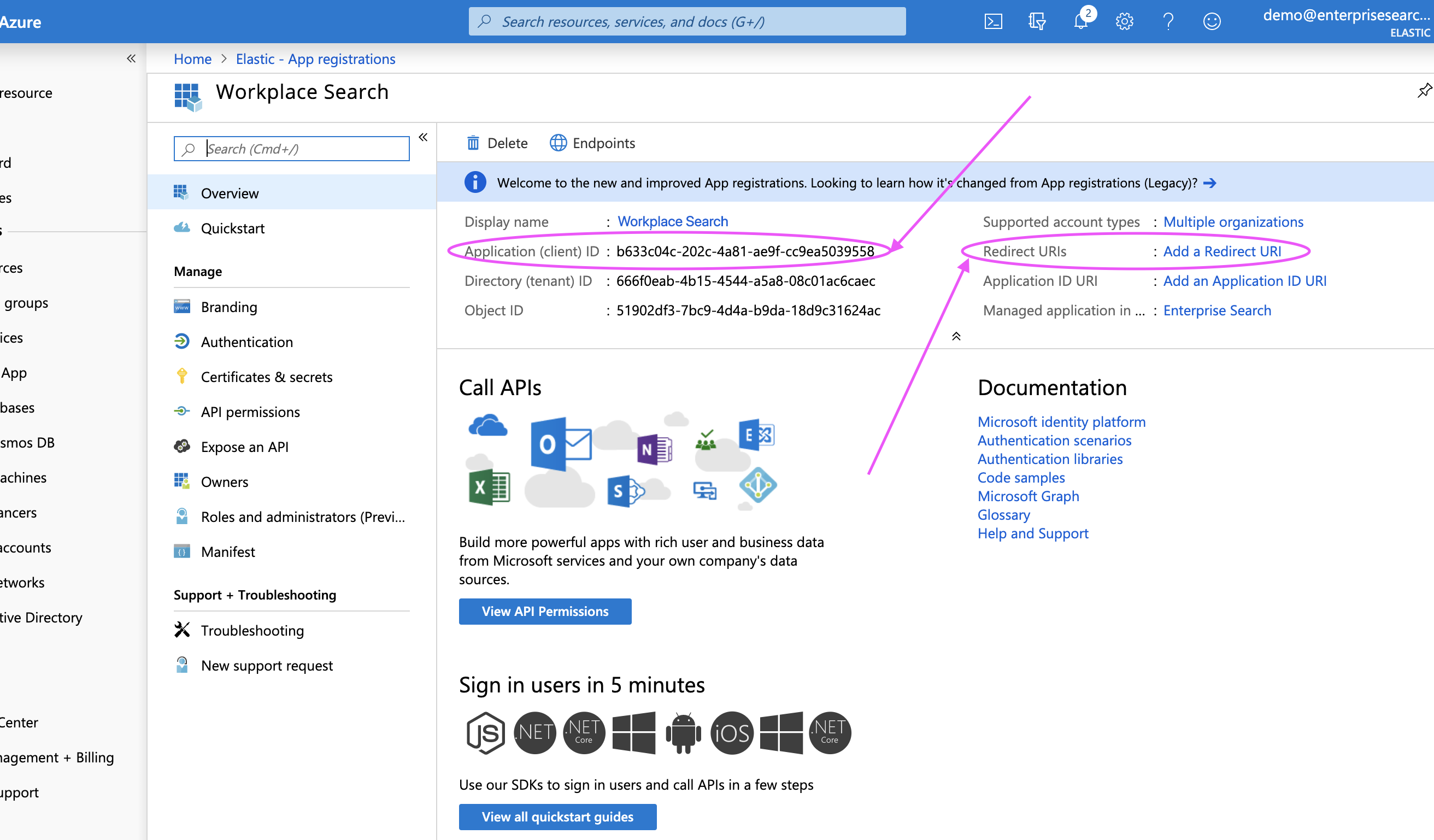
Step 6. Retrieve and keep the Client ID handy - we’ll need it within Workplace Search.
Step 7. Next, click the Add a Redirect URI link in the header.
The redirect URIs required vary by which user interface you are using to manage Enterprise Search. Enterprise Search in Kibana and standalone Enterprise Search use different redirect URIs. See user interfaces for details on each UI.
When using standalone Enterprise Search, add the following two redirect URIs, substituting <WS_BASE_URL> with the base URL at which Workplace Search is hosted (scheme + host, no path).
<WS_BASE_URL>/ws/org/sources/share_point/create <WS_BASE_URL>/ws/sources/share_point/create
Examples:
# Deployment using a custom domain name https://www.example.com/ws/org/sources/share_point/create https://www.example.com/ws/sources/share_point/create # Deployment using a default Elastic Cloud domain name https://c3397e558e404195a982cb68e84fbb42.ent-search.us-east-1.aws.found.io:443/ws/org/sources/share_point/create https://c3397e558e404195a982cb68e84fbb42.ent-search.us-east-1.aws.found.io:443/ws/sources/share_point/create # Unsecured local development environment http://localhost:3002/ws/org/sources/share_point/create http://localhost:3002/ws/sources/share_point/create
When using Enterprise Search in Kibana, use the following redirect URI, substituting <KIBANA_BASE_URL> with the base URL of your Kibana instance. This should correspond with the value of kibana.external_url in your enterprise-search.yml:
<KIBANA_BASE_URL>/app/enterprise_search/workplace_search/sources/added
Examples:
# Deployment using a custom domain name for Kibana https://www.example.com/app/enterprise_search/workplace_search/sources/added # Deployment using a default Elastic Cloud domain name for Kibana https://c3397e558e404195a982cb68e84fbb42.kb.us-east-1.aws.found.io:443/app/enterprise_search/workplace_search/sources/added # Unsecured local Kibana environment http://localhost:5601/app/enterprise_search/workplace_search/sources/added
Step 7. Save the cofiguration:
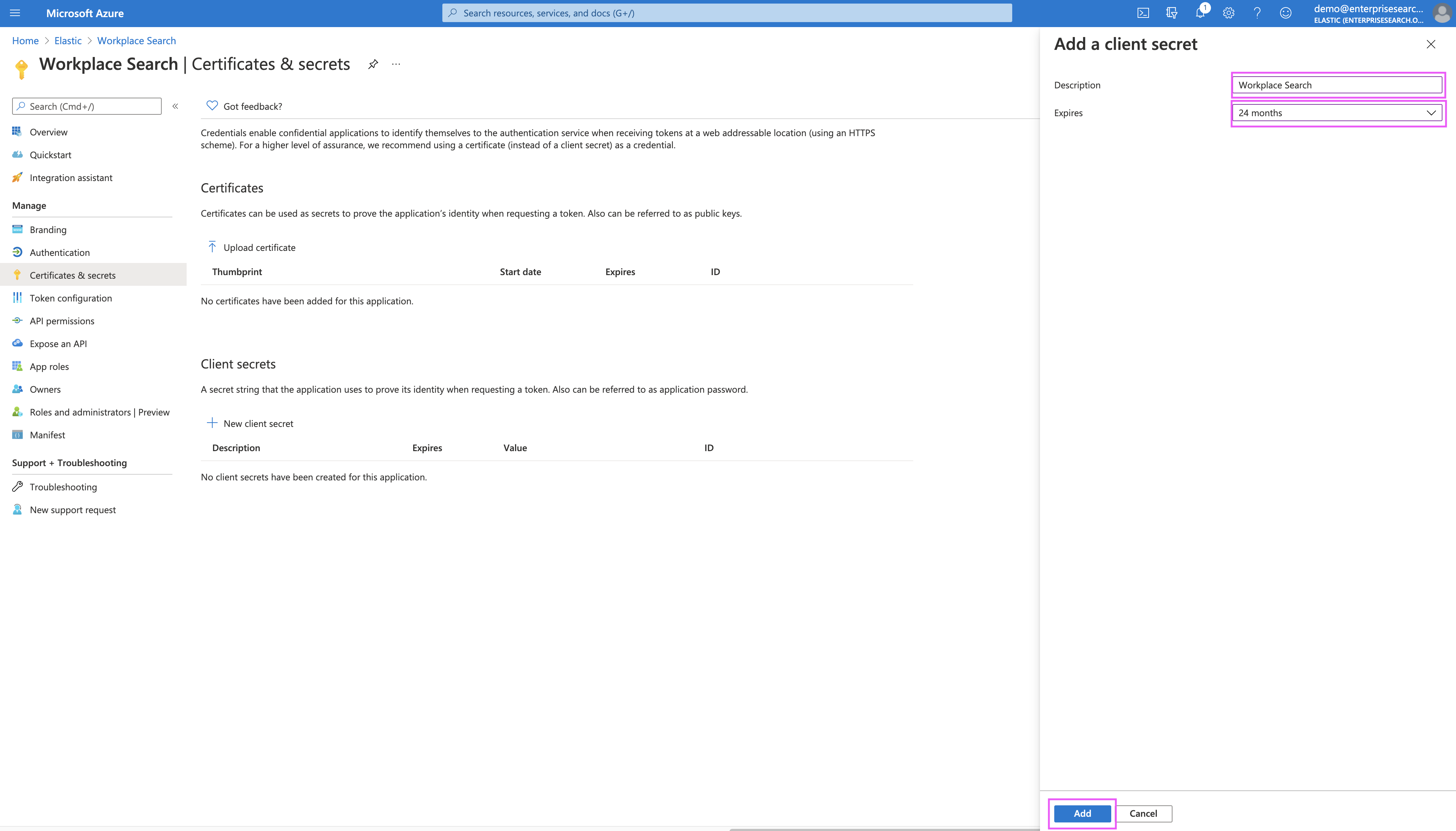
Step 8. Locate the Client Secret by navigating to Certificates & Secrets:
Step 9. Pick a name for your client secret (for example, Workplace Search). Select 24 months as the expiration date:
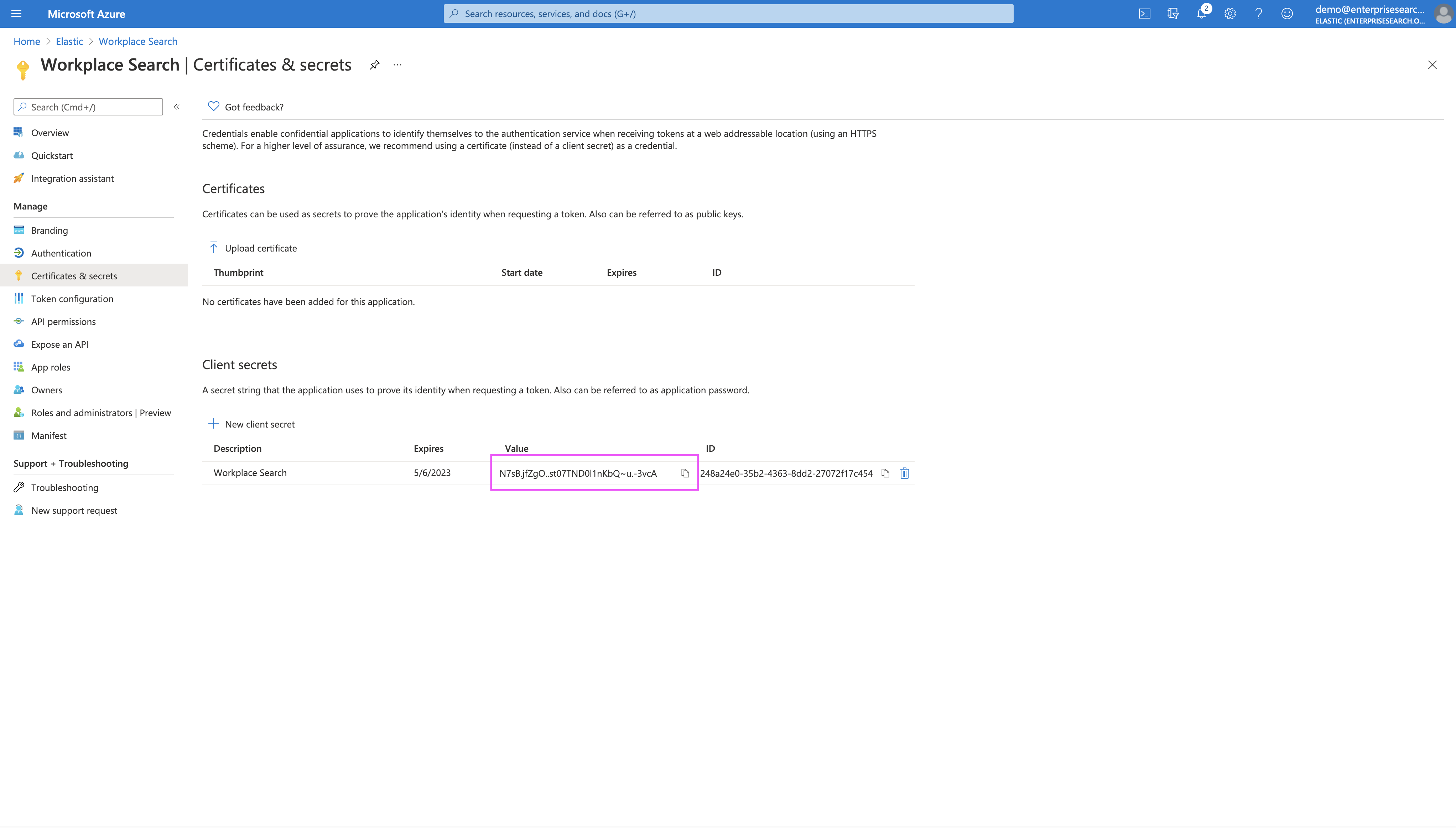
Step 10. Save the Client Secret value before leaving this screen.
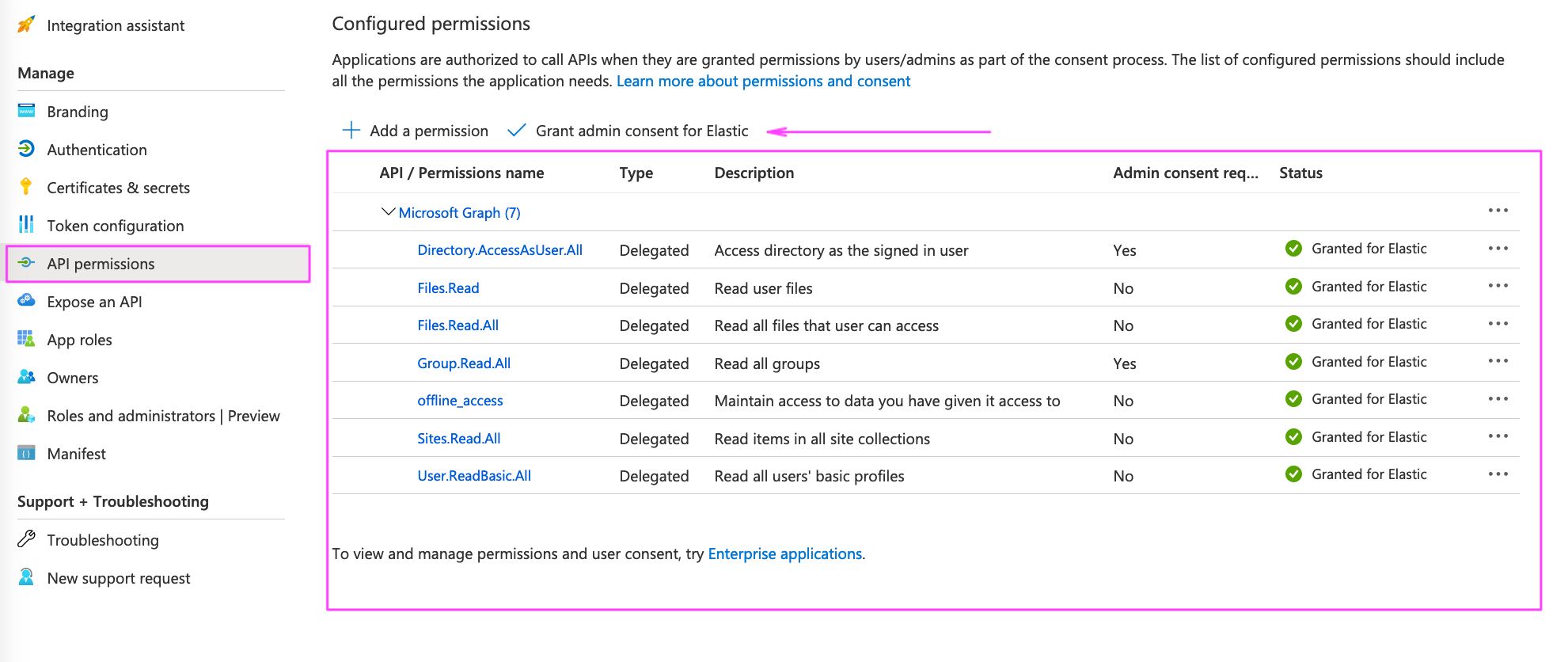
Step 11. We must now set up the permissions the Application will request from the Admin. Navigate to API Permissions and click Add Permission. Add delegated permissions until the list resembles the following:
User.ReadBasic.All Group.Read.All Directory.AccessAsUser.All Files.Read Files.Read.All Sites.Read.All offline_access
Step 12. Finally, Grant admin consent.
Use the Grant Admin Consent link from the permissions screen.
Step 13. From the Workplace Search administrative dashboard’s Sources area, locate SharePoint Online, click Configure and provide both the Client ID and Client Secret.
Voilà! The SharePoint Online connector is now configured, and ready to be used to synchronize content. In order to capture data, you must now connect a SharePoint Online instance with the adequate authentication credentials.
Connecting SharePoint Online to Workplace Search
editOnce the SharePoint Online connector has been configured, you may connect a SharePoint Online instance to your organization.
Step 1. Head to your organization’s Workplace Search administrative dashboard, and locate the Sources tab.
Step 2. Click Add a new source.
Step 3. Select SharePoint Online in the Configured Sources list, and follow the SharePoint Online authentication flow as presented.
Step 4. Upon the successful authentication flow, you will be redirected to Workplace Search.
SharePoint Online content will now be captured and will be ready for search gradually as it is synced. Once successfully configured and connected, the SharePoint Online synchronization automatically occurs every 2 hours.
Document-level permissions
editYou can synchronize document access permissions from SharePoint Online to Workplace Search. This will ensure the right people see the right documents.
See Document-level permissions for Microsoft.
Limiting the content to be indexed
editIf you don’t need to index all the available content, you can specify the indexing rules via the API. This will help shorten indexing times and limit the size of the index. See Customizing indexing.
For SharePoint Online, applicable rule types would be path_template and file_extension.
Synchronized fields
editThe following table lists the fields synchronized from the connected source to Workplace Search. The attributes in the table apply to the default search application, as follows:
- Display name - The label used when displayed in the UI
- Field name - The name of the underlying field attribute
- Faceted filter - whether the field is a faceted filter by default, or can be enabled (see also: Customizing filters)
-
Automatic query refinement preceding phrases - The default list of phrases that must precede a value of this field in a search query in order to automatically trigger query refinement. If "None," a value from this field may trigger refinement regardless of where it is found in the query string. If
'', a value from this field must be the first token(s) in the query string. IfN.A., automatic query refinement is not available for this field by default. All fields that have a faceted filter (defaultorconfigurable) can also be configured for automatic query refinement; see also Update a content source, Get a content source’s automatic query refinement details and Customizing filters.
| Display name | Field name | Faceted filter | Automatic query refinement preceding phrases |
|---|---|---|---|
Id |
|
No |
N.A. |
URL |
|
No |
N.A. |
Title |
|
No |
N.A. |
Type |
|
Default |
None |
Path |
|
No |
N.A. |
Created by |
|
Configurable |
[ |
Last updated |
|
No |
N.A. |
Updated by |
|
Configurable |
[ |
Drive owner |
|
Default |
N.A. |
Media type |
|
Default |
None |
Extension |
|
Default |
None |