Getting started: Protect hosts with endpoint threat intelligence from Elastic Security
editGetting started: Protect hosts with endpoint threat intelligence from Elastic Security
editGo beyond blocking malware, ransomware, and advanced threats. Unify detection, prevention, and response across your entire ecosystem.
This guide walks you through a simple endpoint management scenario so you can learn the basics of creating an Elasticsearch cluster, adding data, and analyzing the results in Kibana. To get started, you can create a deployment in Elastic Cloud, where most of the configuration happens automatically. In just a few steps, you’ll learn how to implement threat intelligence to protect an endpoint and feed security information directly into the Elastic Stack for viewing and monitoring.
In this tutorial, you’ll deploy the Elastic Stack, install an Elastic Agent on your host to protect it from threats and collect logs and metrics, and then visualize the collected information.
If you prefer video tutorials, check out the
Elastic Security Quick Start
or the Elastic Security How-to Series.
Prerequisites
editTo get started, all you need is an internet connection, an email address, and a local or virtual machine from which you’d like to gather some endpoint event data.
Step 1: Create an Elastic Cloud deployment
editIf you’ve already signed up for a trial deployment you can skip this step.
An Elastic Cloud deployment offers you all of the features of the Elastic Stack as a hosted service. To test drive your first deployment, sign up for a free Elastic Cloud trial:
- Go to our Elastic Cloud Trial page.
-
Enter your email address and a password.
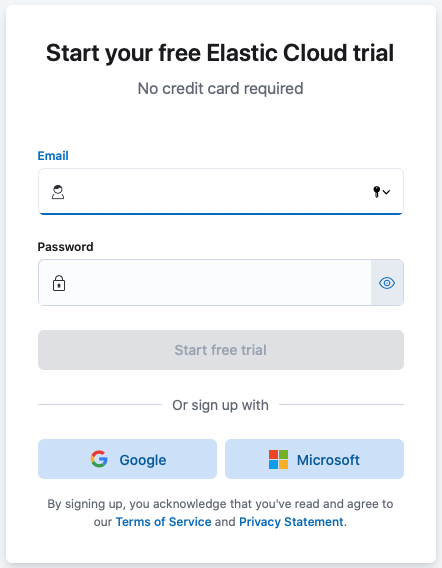
-
After you’ve logged in, you can directly create a deployment. Give your deployment a name and select Create deployment.
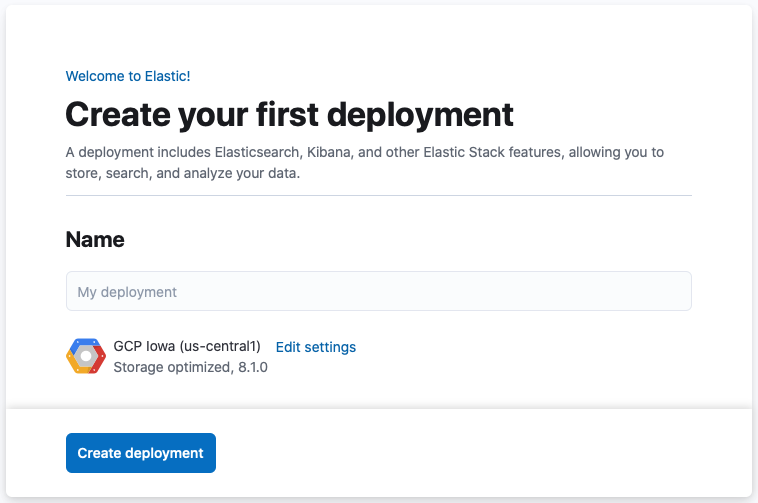
-
While the deployment sets up, make a note of your
elasticsuperuser password and keep it in a safe place. - Once the deployment is ready, select Continue. At this point, you access Kibana and are prompted to Add integrations or to Explore on your own. Feel free to check the various options and integrations available. You can return to the home page of Kibana at any time by selecting the Elastic logo.
Your deployment includes a pre-configured instance of Fleet Server, which manages the Elastic Agents that you can use to monitor a host system.
Step 2: Add the Endpoint Security integration
editElastic integrations include the configuration necessary to collect data from systems, manage systems, and perform actions with external systems. For example, there are integrations to collect MySQL logs and metrics, to protect hosts from malware, and to create issues in incident-reporting systems.
-
Go to the Kibana home page and select Add integrations.
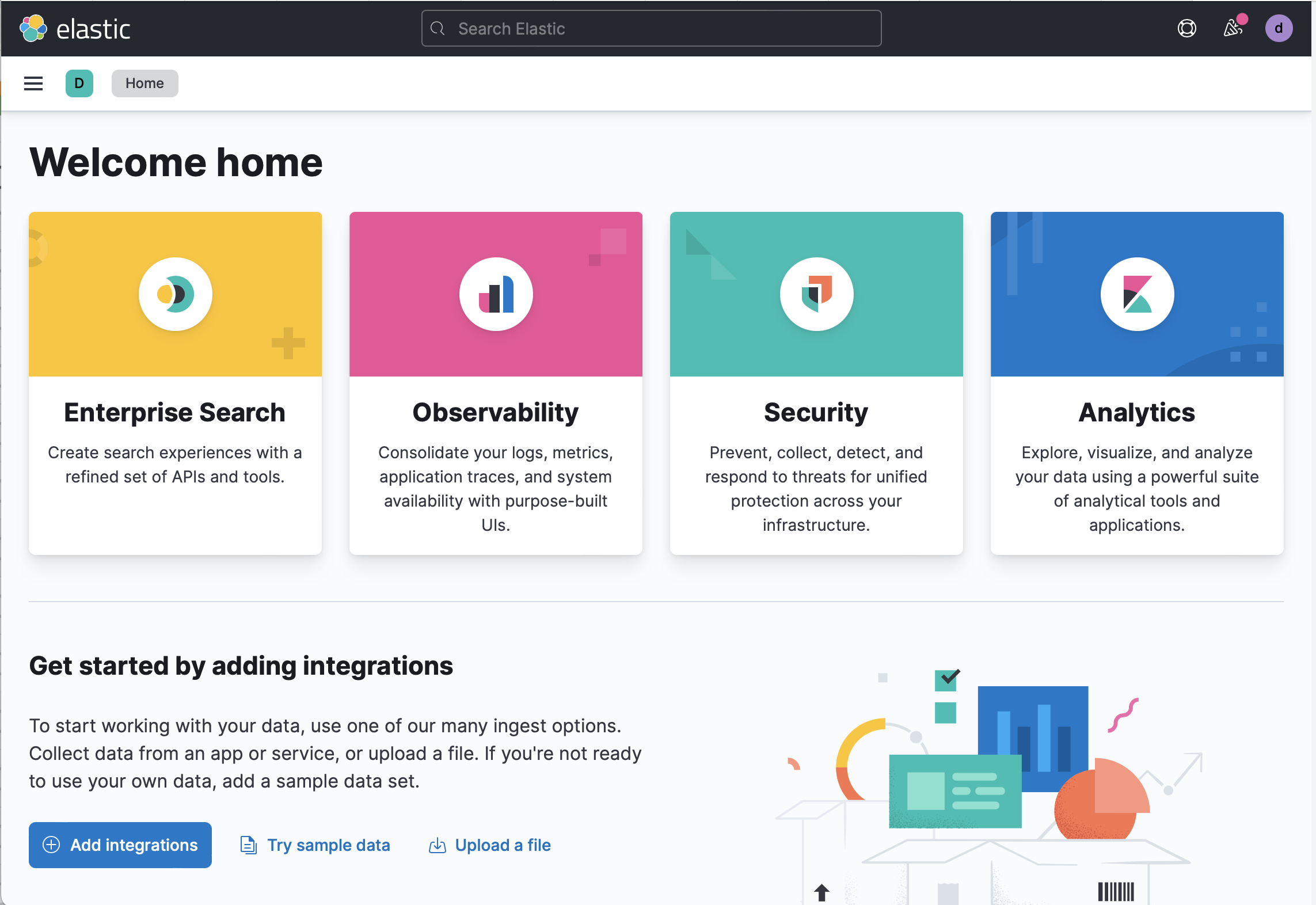
- Select Endpoint Security and on the next page select Add Endpoint Security.
-
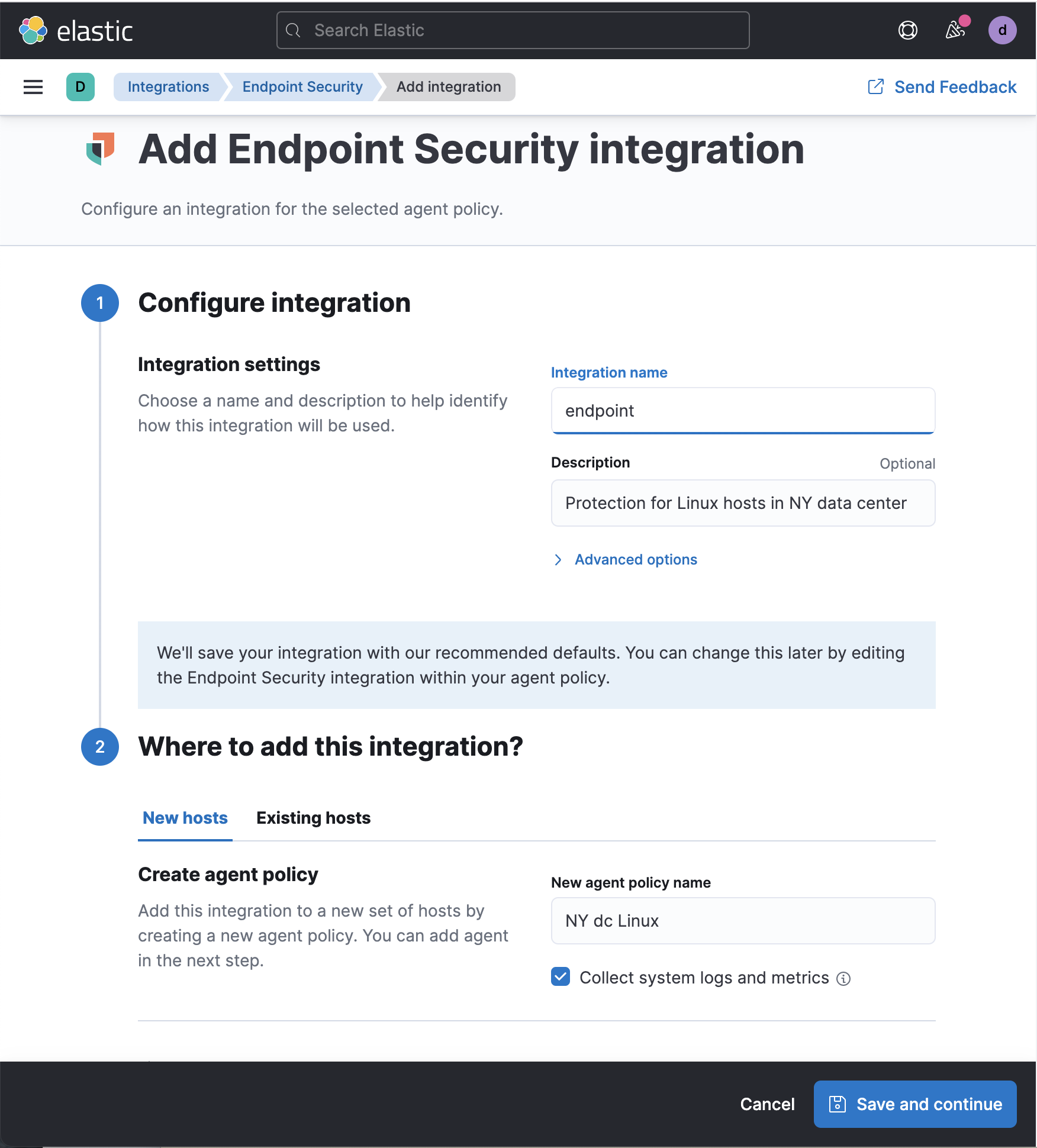
Add details for this integration:
-
Give the integration a name — since this is an integration to
protect your hosts, you might name it
endpoint security. - Integrations get associated with Agent policies. Give the policy a name — you might apply this policy to all of the Linux hosts in a particular data center and name it for the operating system and location.
- The Elastic Agent can protect your host and collect logs and metrics at the same time. Make sure that Collect system logs and metrics is enabled.
-
Select Save and continue. This step takes a minute or two to complete.
-
Give the integration a name — since this is an integration to
protect your hosts, you might name it
- Select Add Elastic Agent to your hosts and the Add agent flyout will be displayed.
Step 3: Install and run an Elastic Agent on your machine
editElastic Agent is a single, unified way to add monitoring for logs, metrics, and other types of data to a host. It can also protect hosts from security threats, query data from operating systems, and more. A single agent makes it easy and fast to deploy monitoring across your infrastructure. Each agent has a single policy (a collection of input settings) that you can update to add integrations for new data sources, security protections, and more.
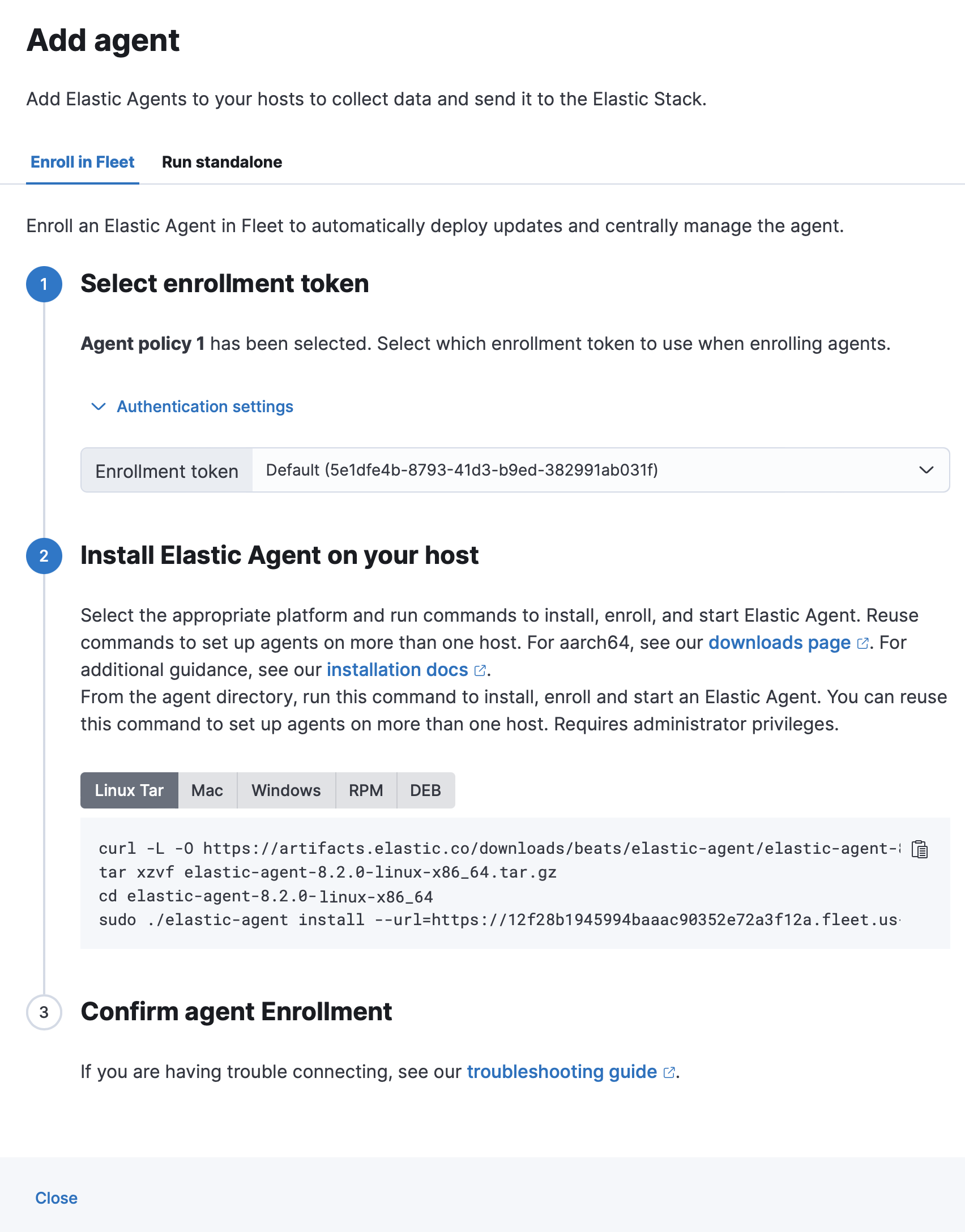
The Add agent flyout has two tabs: Enroll in Fleet and Run standalone. The default is to enroll the agents in Fleet, as this reduces the amount of work on the person managing the hosts by providing a centralized management tool in Kibana.
- Skip the Select enrollment token step, but note that the enrollment token is specific to the Agent policy that you just created. When you run the command to enroll the agent with Fleet you will pass in the enrollment token.
- Download, install, and enroll the Elastic Agent on your host by following the Install Elastic Agent on your host step.
-
After about a minute your agent will have enrolled with the server, downloaded the configuration specified in the policy that you just created, and started collecting data. Close the Add agent flyout.
Step 4: View your host in Elastic Security
edit- Go back to the Kibana home page (select the Elastic logo).
-
Open Security.
-
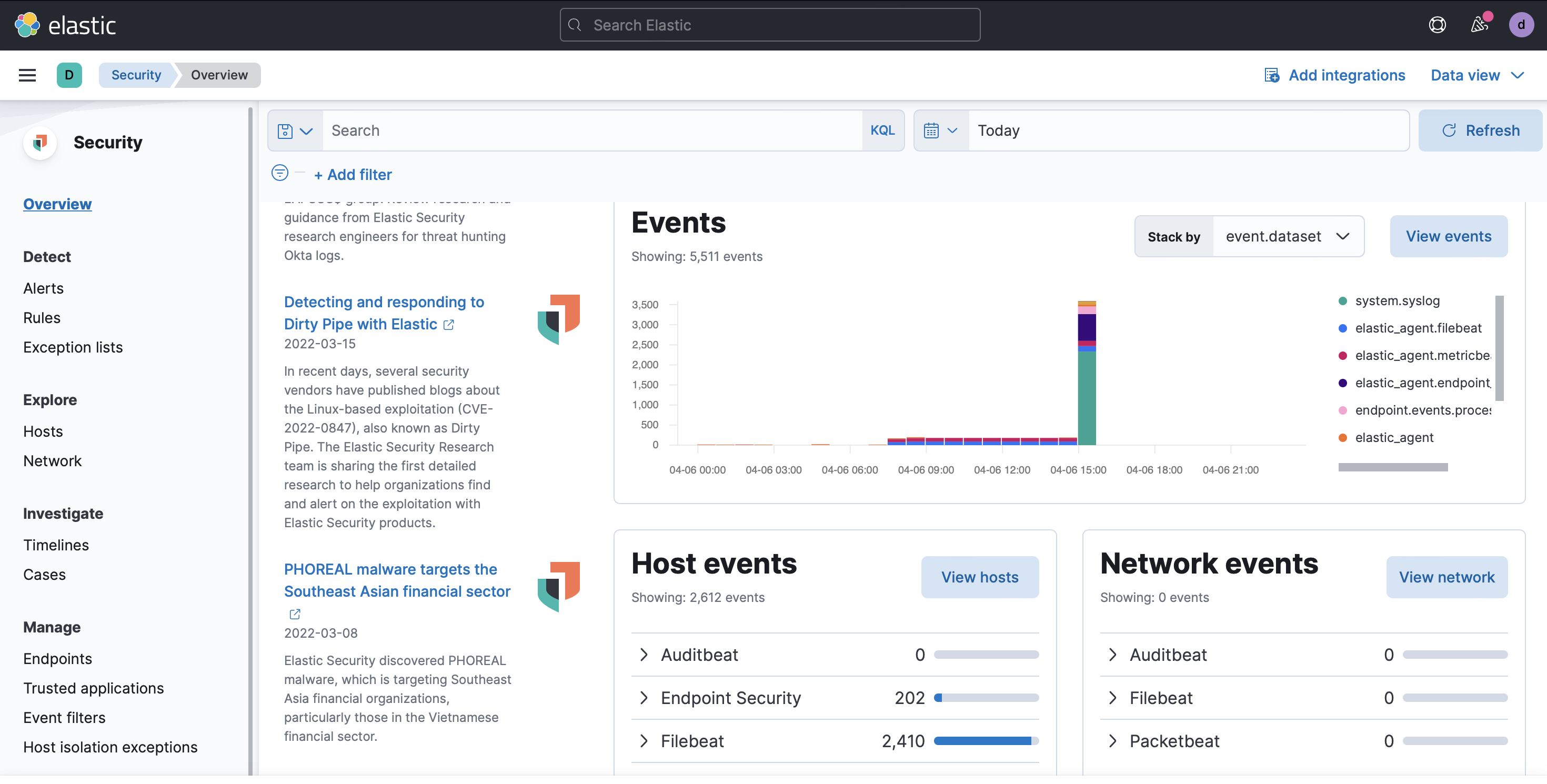
From the navigation pane, open the Overview page. On the overview page you probably will not have any alerts, so scroll down to the Events section, just to verify that data is flowing. It may take a minute for events to show, as when the Elastic Agent enrolls for the first time the configuration is being copied down from the server before collection starts.
-
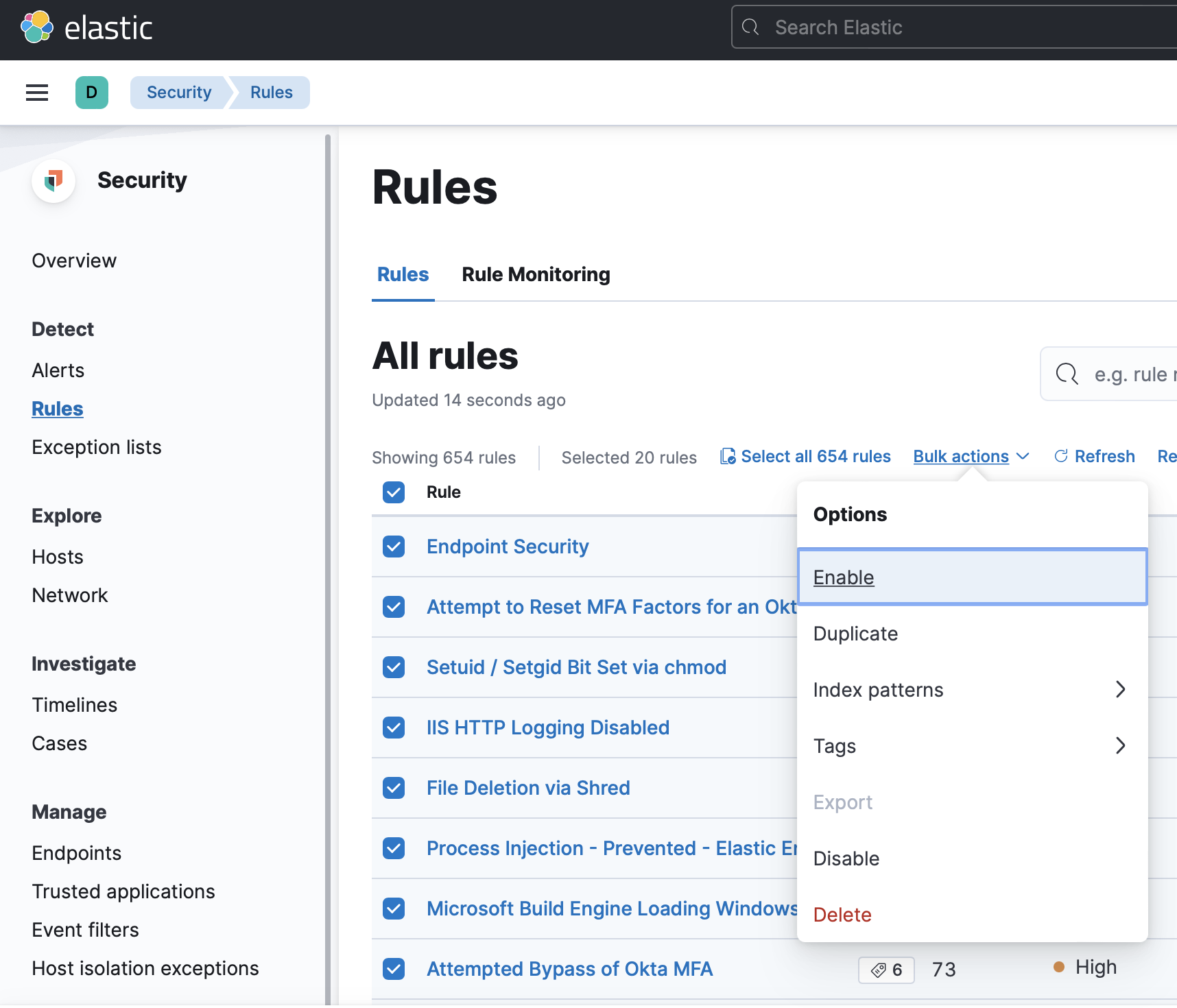
Now, enable detection rules by going back to the navigation pane and opening the Rules page. You should tailor the rules that you enable based on your organization’s resources and needs. For this tutorial, choose some or all of the rules and select Bulk actions and then Enable.
Step 5: Generate an alert
editThe European Institute for Computer Anti-Virus Research (EICAR) provides anti malware test files. If your company policy allows these to be used, then proceed with this step.
- Navigate to eicar.org and use the button to download an anti malware testfile.
-
Download
eicar_com.zipto the system on which you installed Elastic Agent.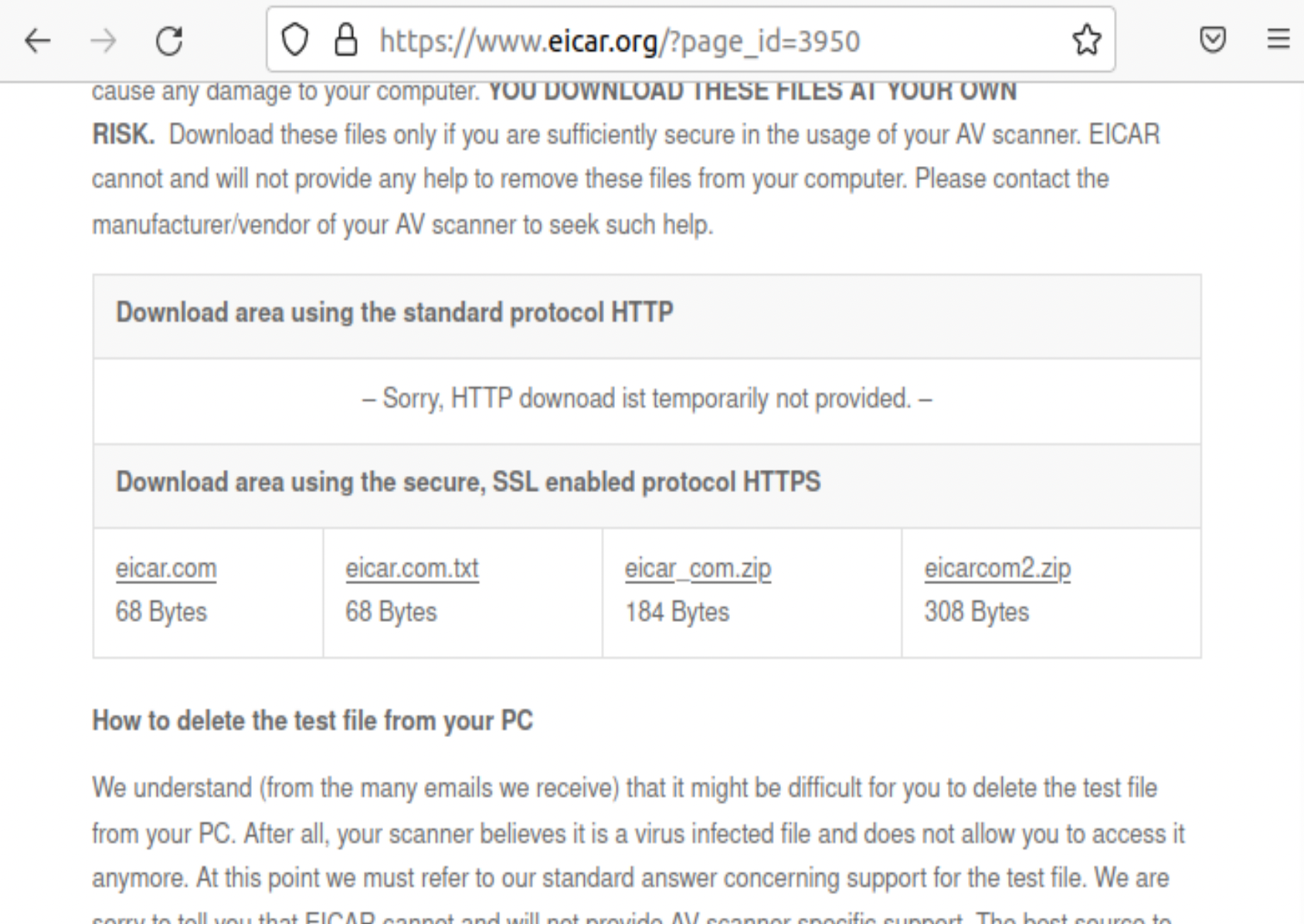
-
Extract the test file and then return to the Security > Detect > Alerts page in Kibana.
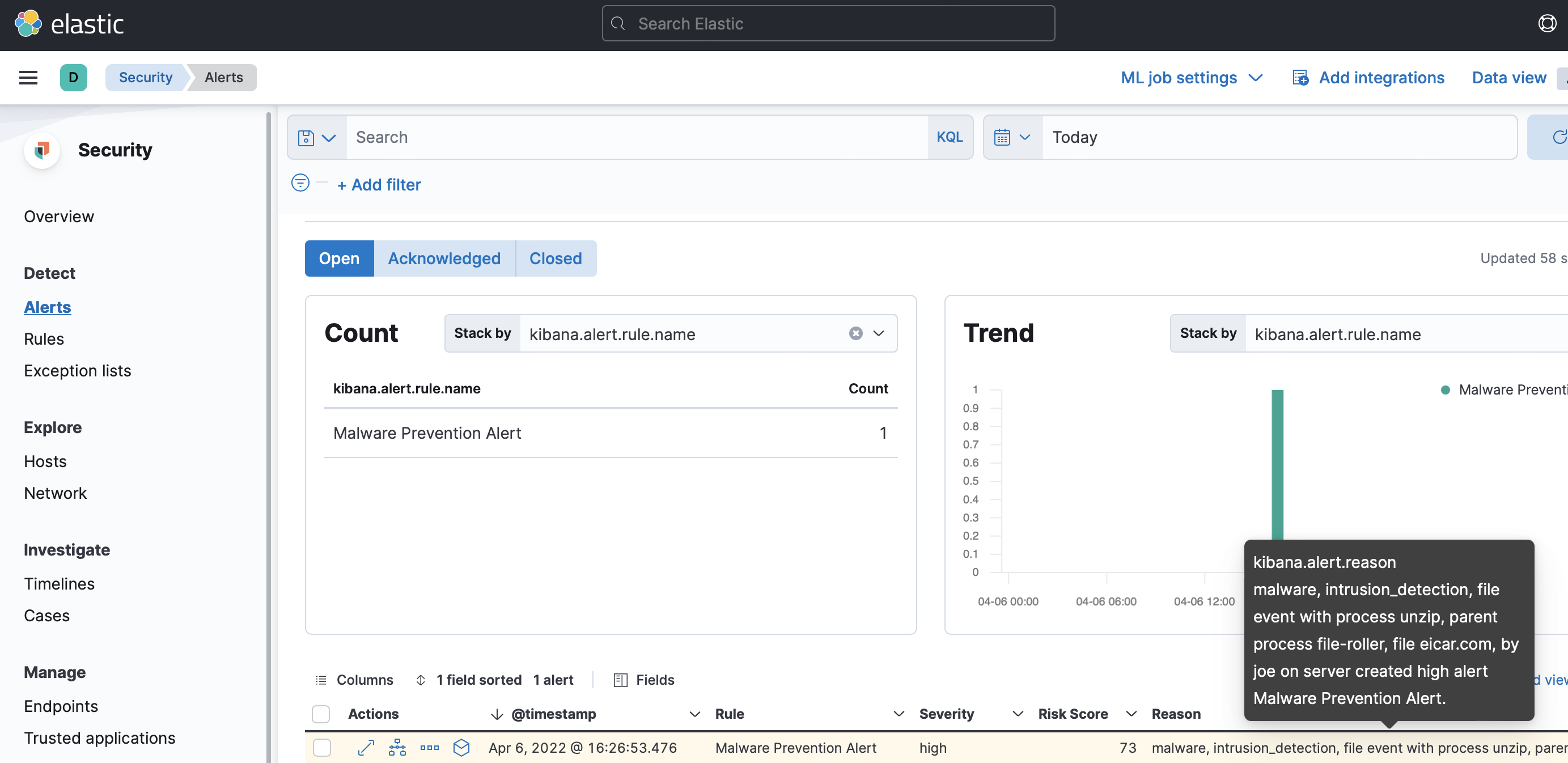
-
You should get a malware prevention alert. Get the details by selecting the View details arrow button.
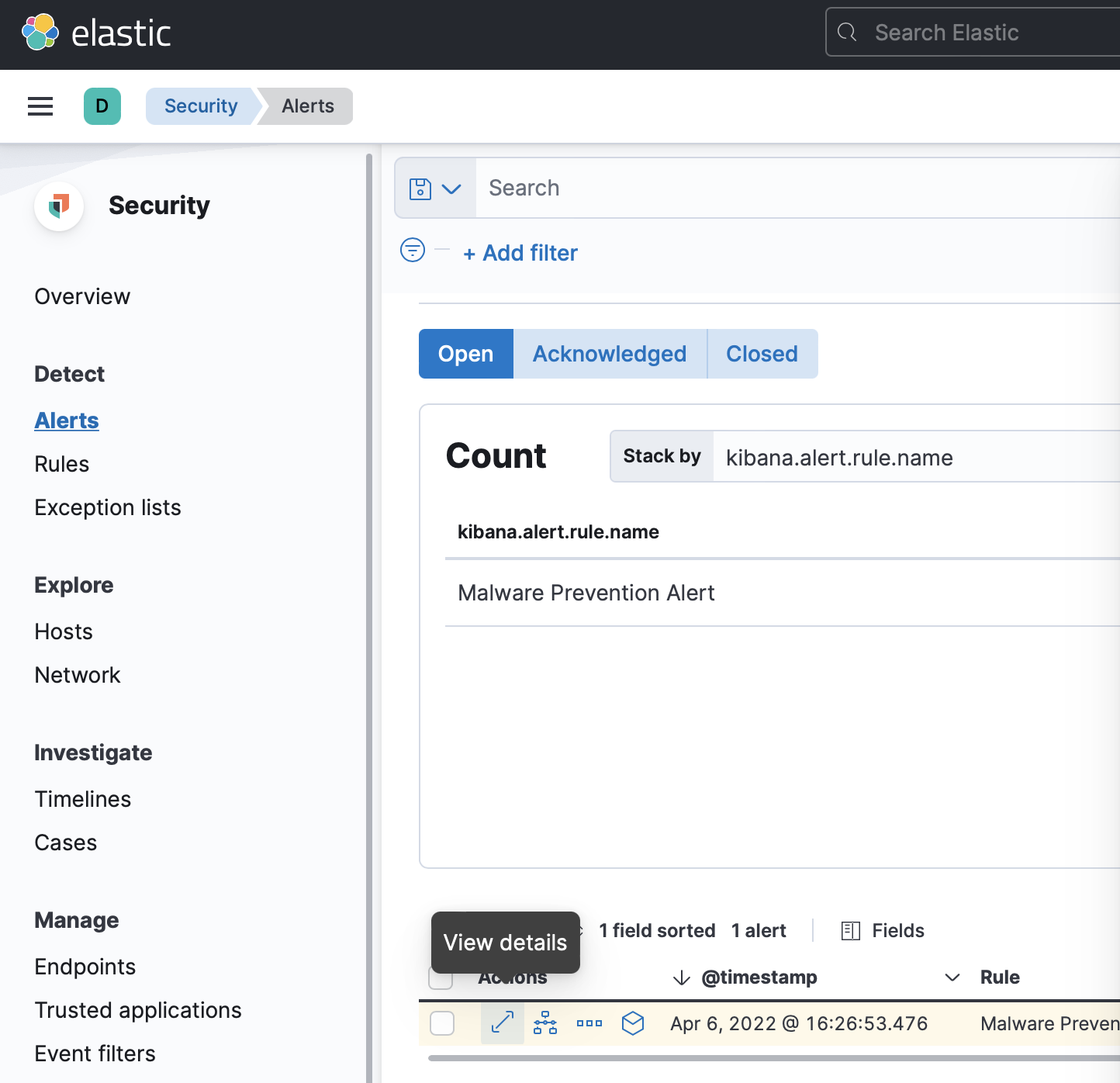
-
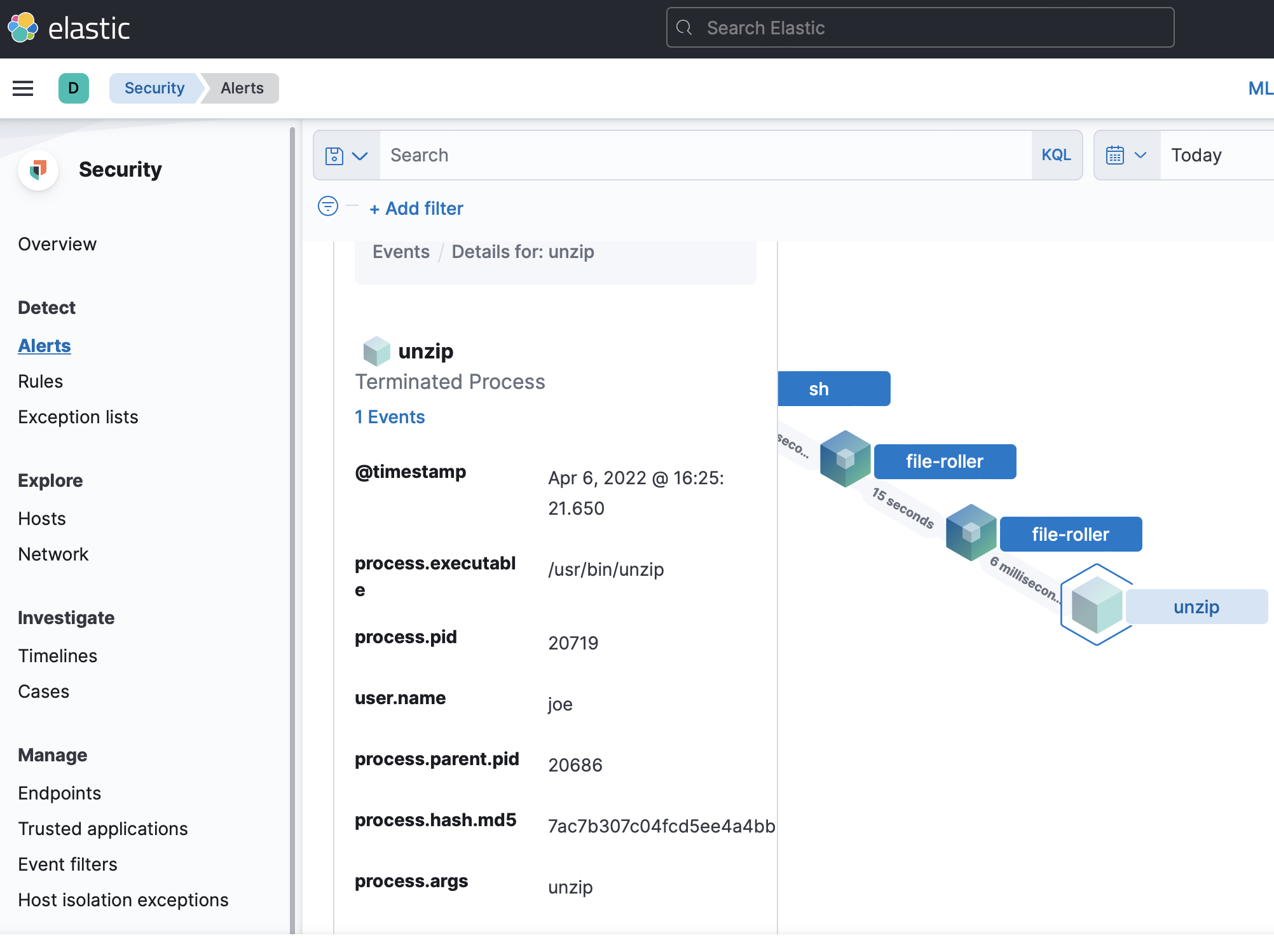
To find out what preceded the event, close the details pop-up and select the Analyze event cube-shaped button. Use the zoom in and out buttons, and drag the window contents around to see what led up to the malware being detected. For example, if you are protecting an Ubuntu endpoint, you may notice that a process named
file-rollerwas used to rununzip. Selecting unzip will show you the timestamp, path to the unzip binary, process ID, username, and more information.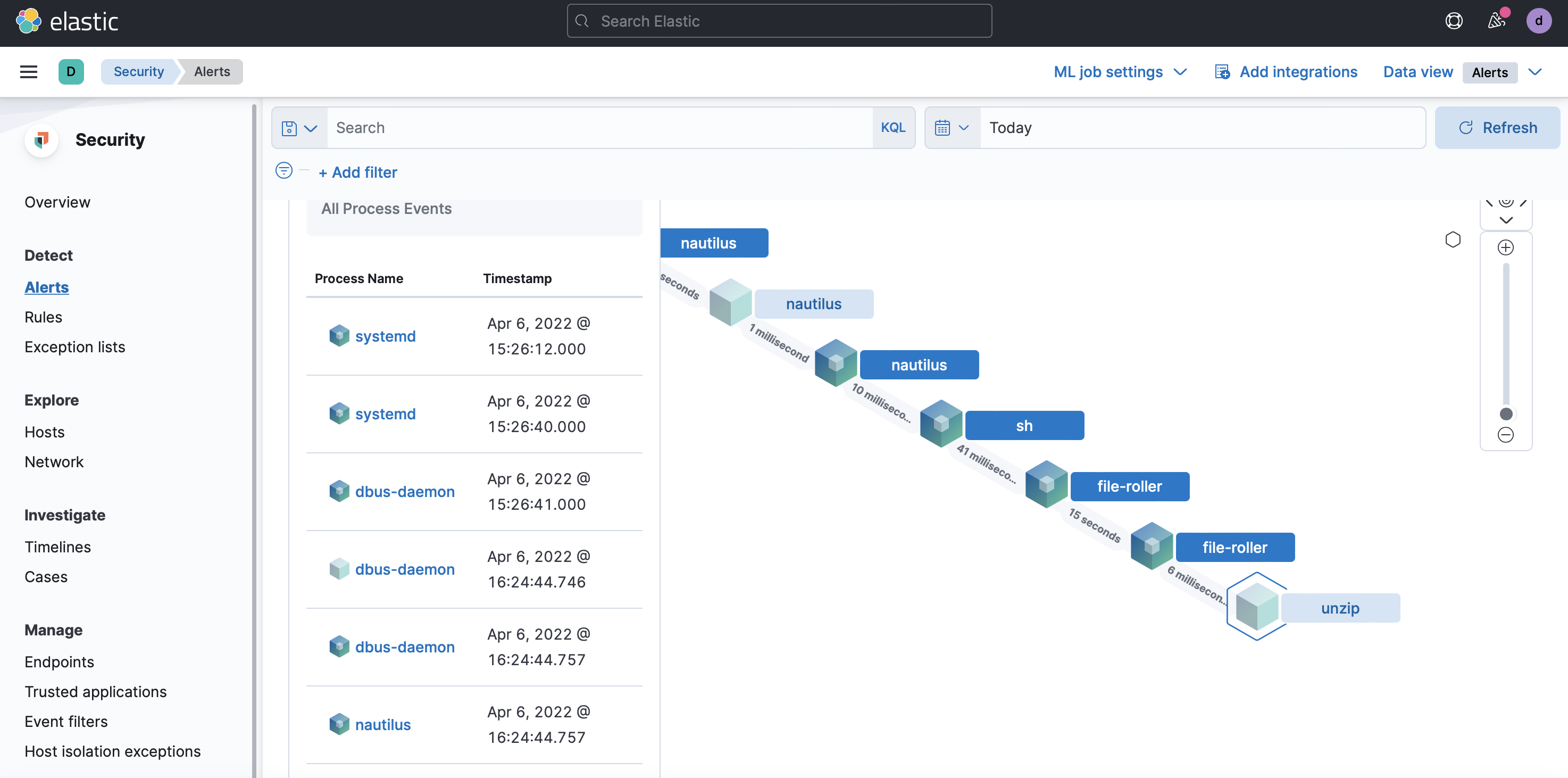
Step 7: Tidying up
edit-
You’ve now learned how to set up an Elastic Cloud deployment and bring in data from a host system to protect endpoints with threat intelligence. If you’d like to remove Elastic Agent from your system, run the
uninstallcommand from the directory where it’s running and then follow the prompts.You must run this command as the root user.
sudo /Library/Elastic/Agent/elastic-agent uninstall
You must run this command as the root user.
sudo /opt/Elastic/Agent/elastic-agent uninstall
Open a PowerShell prompt as an Administrator (right-click the PowerShell icon and select Run As Administrator).
From the PowerShell prompt, run:
C:\"Program Files"\Elastic\Agent\elastic-agent.exe uninstall
If you run into any problems, check Uninstall Elastic Agents from edge hosts for the detailed uninstall steps.
- You can also remove the anti malware test file if you downloaded that.
What’s next?
editLearn more about Elastic Security
- Check out the How-to Series:Elastic Security.
- Enroll in a free Elastic Security Fundamentals:SIEM course.
- Learn more in the docs.
- Got everything working as you want it? Roll out your agent policies to other hosts by deploying Elastic Agents across your infrastructure!
Learn about other Elastic solutions and features
- Want to add search to your website, applications, or organization data? Try out Enterprise Search.
- Want Elastic to do the heavy lifting? Use machine learning to detect anomalies.