Findings page
editFindings page
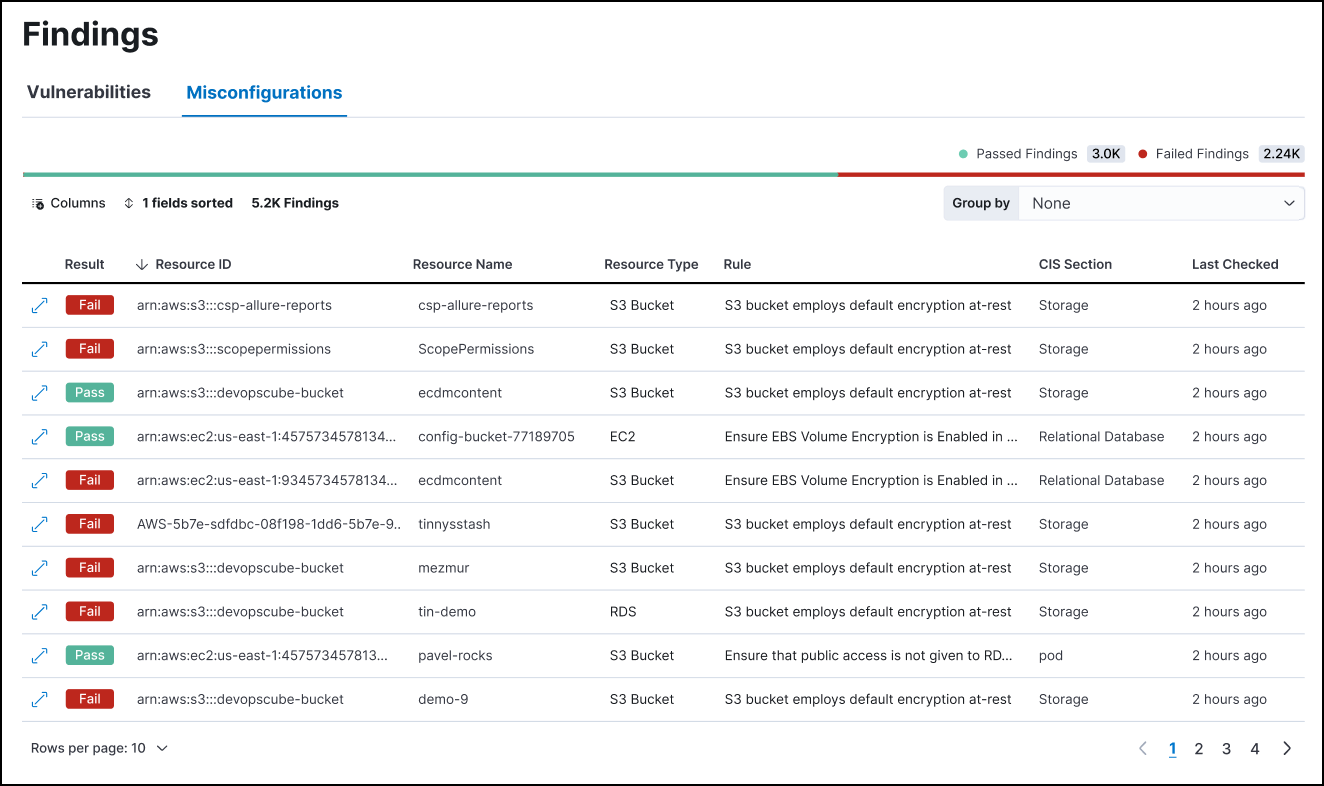
editThe Findings page displays the configuration risks identified by the CSPM and KSPM integrations.
What are KSPM findings?
editKSPM findings indicate whether a given resource passed or failed evaluation against a specific security guideline. Each finding includes metadata about the resource evaluated and the security guideline used to evaluate it. Each finding’s result (pass or fail) indicates whether a particular part of your infrastructure meets a security guideline.
Group and filter findings
editBy default, the Findings page lists all findings, without grouping or filtering.
Group findings by resource
edit- Select Group by → Resource to display a list of resources sorted by their total number of failed findings.
- Click a resource ID to display the findings associated with that resource.
Filter findings
editYou can filter findings data in two ways:
-
The KQL search bar: For example, search for
result.evaluation : failedto view all failed findings. - In-table value filters: Hover over a finding to display available inline actions. Use the Filter In (plus) and Filter Out (minus) buttons.
Customize the Findings table
editUse the toolbar buttons in the upper-left of the Findings table to customize the columns you want displayed:
- Columns: Select which columns to display.
- x fields sorted: Sort the table by one or more columns.
Remediate failed findings
editTo remediate failed findings and reduce your attack surface:
- First, filter for failed findings.
- Click the arrow to the left of a failed finding to open the findings flyout.
-
Follow the steps under Remediation.
Remediation steps typically include commands for you to execute. These sometimes contain placeholder values that you must replace before execution.
Generate alerts for failed Findings
editYou can create detection rules that detect specific failed findings directly from the Findings page.
- Click the arrow to the left of a Finding to open the findings flyout.
- Click Take action, then Create a detection rule. This automatically creates a detection rule that creates alerts when the associated benchmark rule generates a failed finding.
- To review or customize the new rule, click View rule.