Elastic Security 7.5.0 released
Editor’s Note — August 19, 2020: The Elastic Endpoint Security and Elastic SIEM solutions mentioned in this post are now referred to as Elastic Security. The broader Elastic Security solution delivers endpoint security, SIEM, threat hunting, cloud monitoring, and more.
Elastic Security combines the threat hunting and analytics of Elastic SIEM with the prevention and response provided by Elastic Endpoint Security. Read on to see how we are helping our customers maximize the effectiveness of their existing security program.
We launched Elastic Endpoint Security after joining forces with Endgame. It is now available as a standard component of our Enterprise subscription, deployable to all of your endpoints — whether 100 or 100,000 — at no additional cost. Elastic Endpoint Security prevents attacks and brings security events and alerts into the Elastic Stack, alongside data from your security tools, observability tools, and other data sources. Centralizing this rich data in Elastic SIEM arms your practitioners to monitor and hunt for undiscovered attacks and respond quickly — stopping threats before damage or loss.
“We value speed of response and the ability to learn from and analyze our historical data. Elastic Endpoint Security has dramatically dropped our mean time to remediate from seven days to 30 minutes over legacy antivirus, and the Elastic Stack has provided an unparalleled way to store, analyze, and react to data well beyond any competitor in the market,” said Andrew Stokes, Assistant Director and Information Security Officer at Texas A&M University. “Combining Elastic Endpoint Security and the Elastic Stack into a single, intelligence-led platform will further simplify and automate our security operations.”
Let’s dive into the updates to Elastic SIEM and Elastic Endpoint Security in 7.5.
Elastic SIEM
Elastic SIEM is better than ever in version 7.5 of the Elastic Stack. What have we been building since Elastic SIEM 7.4?
Identify threats by ingesting security data from Elastic Endpoint Security
Version 7.5 of Elastic SIEM supports data from Elastic Endpoint Security (previously Endgame). SIEM users who have deployed Elastic Endpoint Security will now have a rich set of endpoint data at their fingertips. The SIEM app’s Overview, Hosts, and Network pages are automatically populated with endpoint event data to reveal anomalous, suspicious, and malicious activity. Further, the Timeline and Events tables have been spiffed up to present DNS, file, network, authentication, and process events in a more curated way — a win for all ECS-compliant host data.
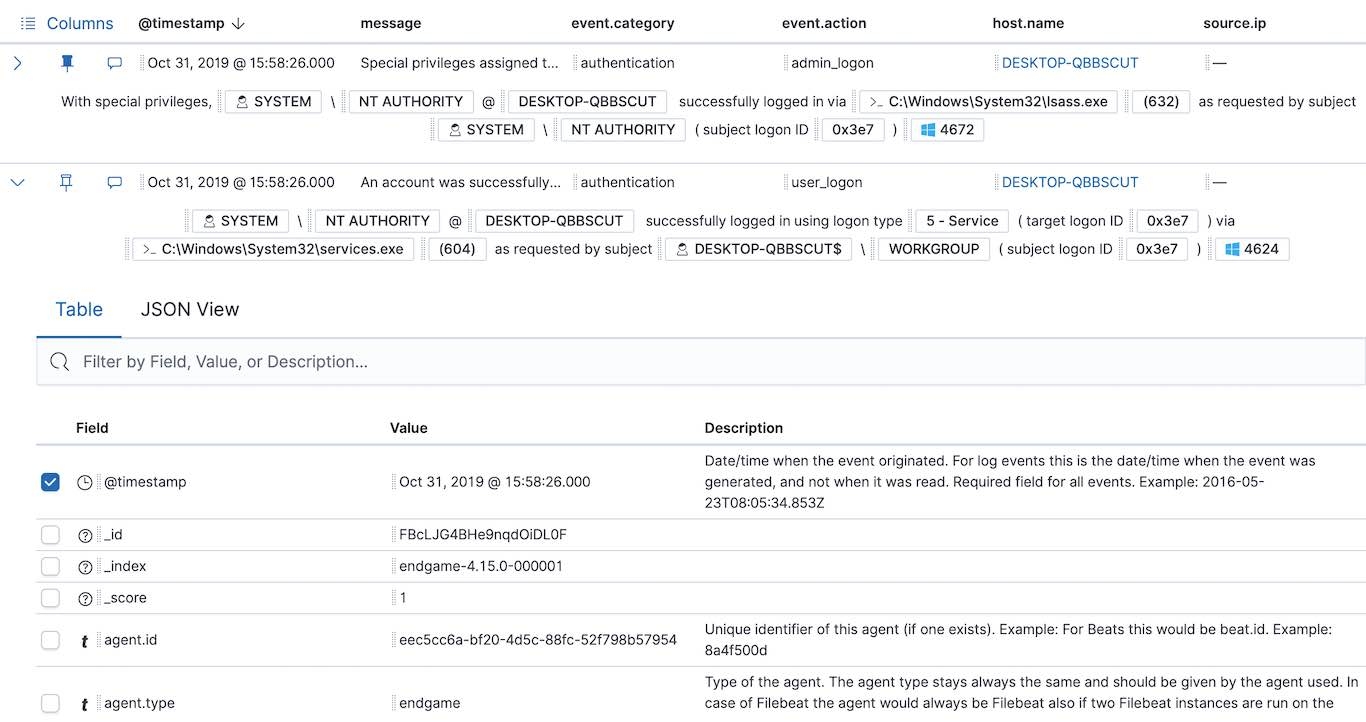
Deploy our latest SecOps anomaly detection content
The Elastic Security team has developed seven new machine learning jobs for Elastic SIEM. This is our third consecutive release providing new content engineered to automatically detect anomalous activity meriting investigation by security operations or threat hunting teams. Learn about these new machine learning jobs here:
| New ML job | OS | Description |
|---|---|---|
| DNS tunneling | Windows, Linux | Reveals unusually large numbers of DNS queries for a single top-level DNS domain, which is often used for DNS tunneling |
| Rare DNS question | Windows, Linux | Reveals rare and unusual DNS queries that indicate network activity with unusual domains is about to occur, which can be due to initial access, persistence, command-and-control, or exfiltration activity |
| Rare URLs | Windows, Linux | Reveals rare and unusual URLs that indicate unusual web browsing activity, which can be due to initial access, persistence, command-and-control, or exfiltration activity |
| Rare server domain | Windows, Linux | Reveals rare and unusual DNS queries that indicate network activity with unusual domains is about to occur, which can be due to initial access, persistence, command-and-control, or exfiltration activity |
| Rare user agent | Windows, Linux | Reveals rare and unusual user agents that indicate web browsing activity by an unusual process other than a web browser, which can be due to persistence, command-and-control, or exfiltration activity |
| Rare remote logins | Windows | Reveals unusual RDP logins, which can indicate account takeover or credentialed persistence using compromised accounts |
| Unusual user context switches | Windows | Reveals user context switches using the runas command or similar techniques, which can indicate account takeover or privilege escalation using compromised accounts |
Elastic SIEM is now supported with 23 pre-built machine learning jobs. Want to configure a custom ML job to surface anomalies in the SIEM app? Simply add it to the SIEM job group. Review our documentation for further information.
Hunt for threats with an enhanced UI
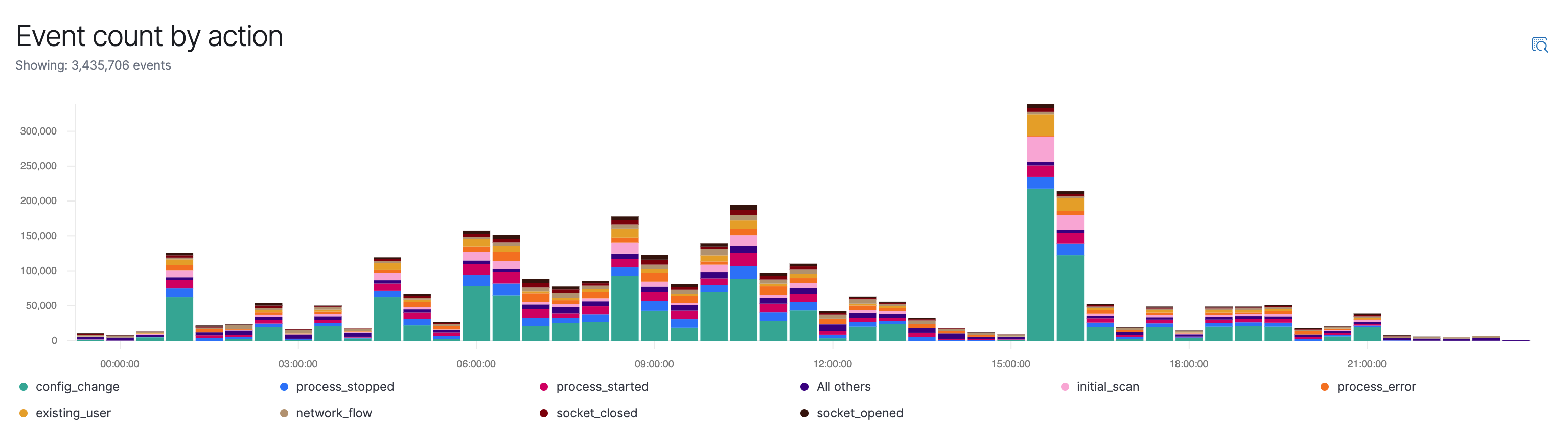
The SIEM app surfaces data to security analysts via three new UI widgets:
The Event histogram widget on the Host and Host detail pages allows you to see events over time for your entire environment or specific hosts.
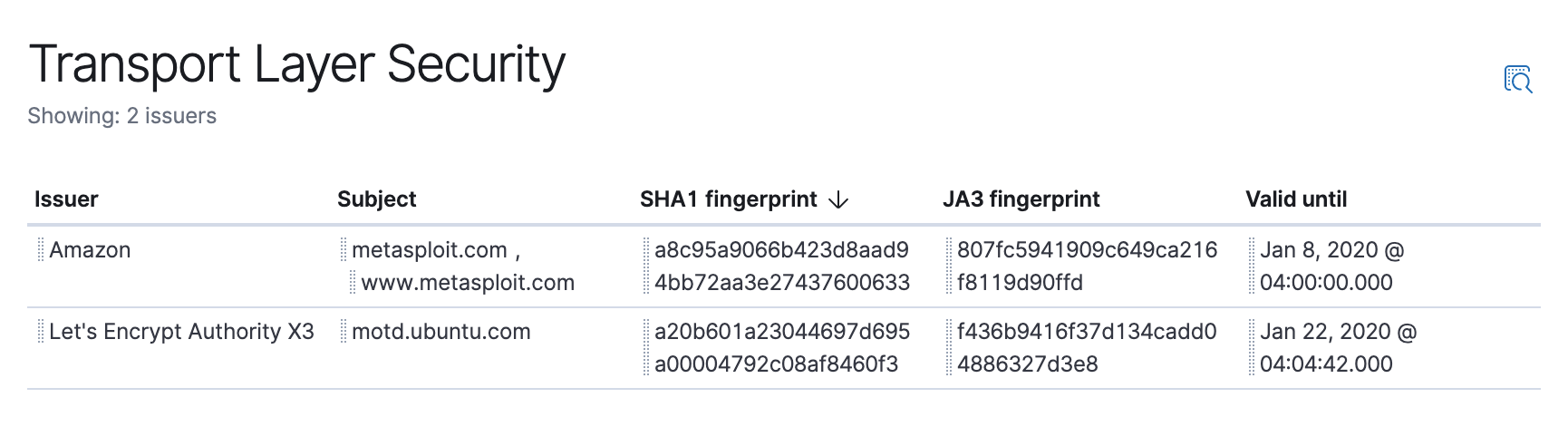
The TLS widget on the Network page makes it easier to hunt based on unusual certificates, such as by JA3 hash.
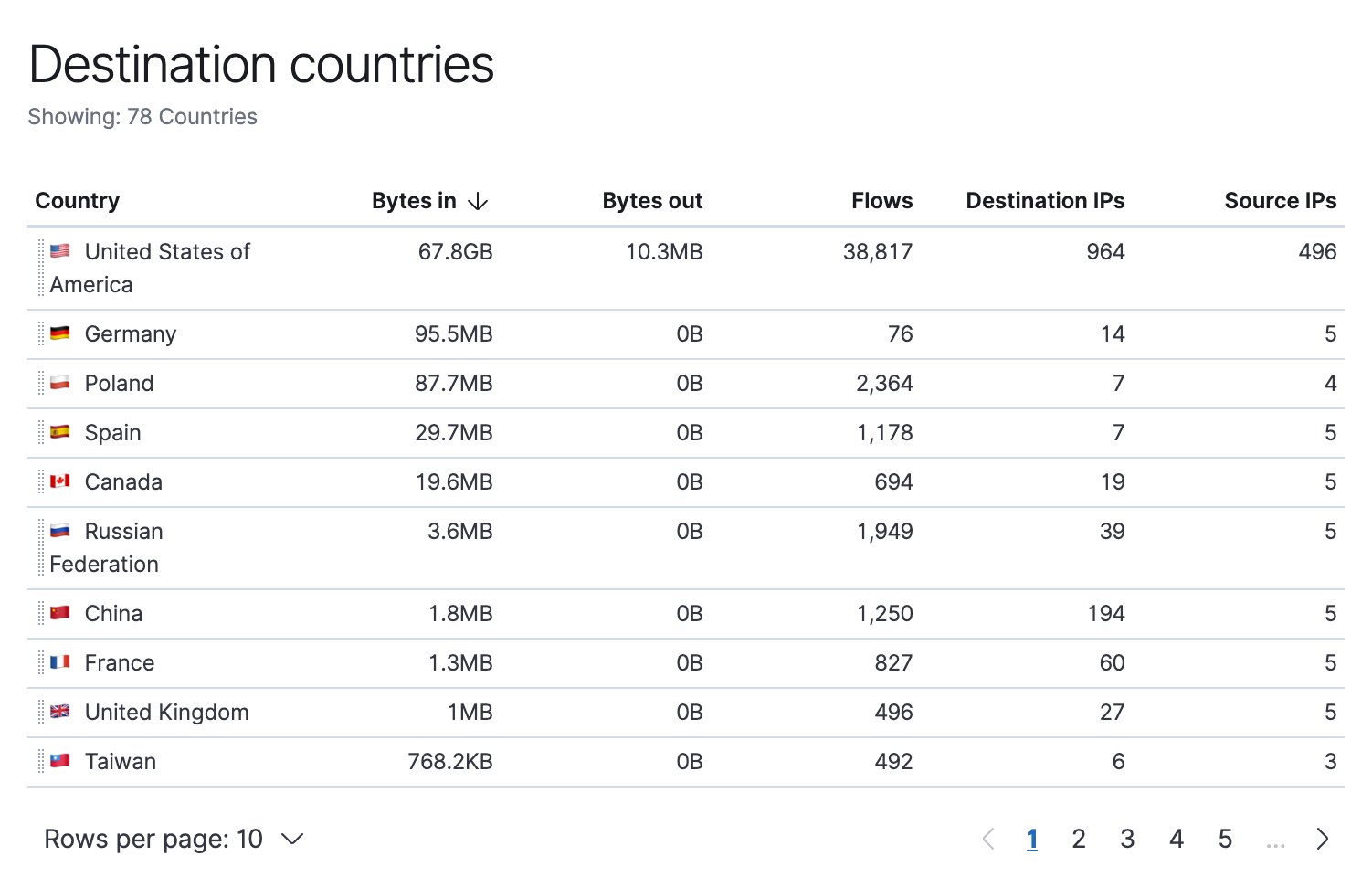
New widgets on the Network and IP Details pages show the source country and destination country of network data, supporting security monitoring and threat hunting.
Elastic Endpoint Security
We are happy to announce that our Endpoint Security product updates will now be released alongside the Elastic Stack. Customers with an Enterprise subscription can implement endpoint protection and endpoint detection and response, protecting their endpoints from known and unknown malware, ransomware, advanced exploits, and memory-level attacks.
Elastic Endpoint Security also simplifies root-cause analysis, incident scoping, and response with features like automated attack visualization, activity, events, and behaviors mapped to the MITRE ATT&CK matrix for faster analysis and triage. It also brings real-time, one-click endpoint isolation to contain threats and preserve endpoint data for investigation.
This latest release of Elastic Endpoint Security, available to Enterprise subscription customers, builds upon these features by deepening the integration with the Elastic Stack and providing additional collaboration tools. To learn more, visit the Elastic Endpoint Security webpage and watch Elastic CEO Shay Banon discuss our Security solution.
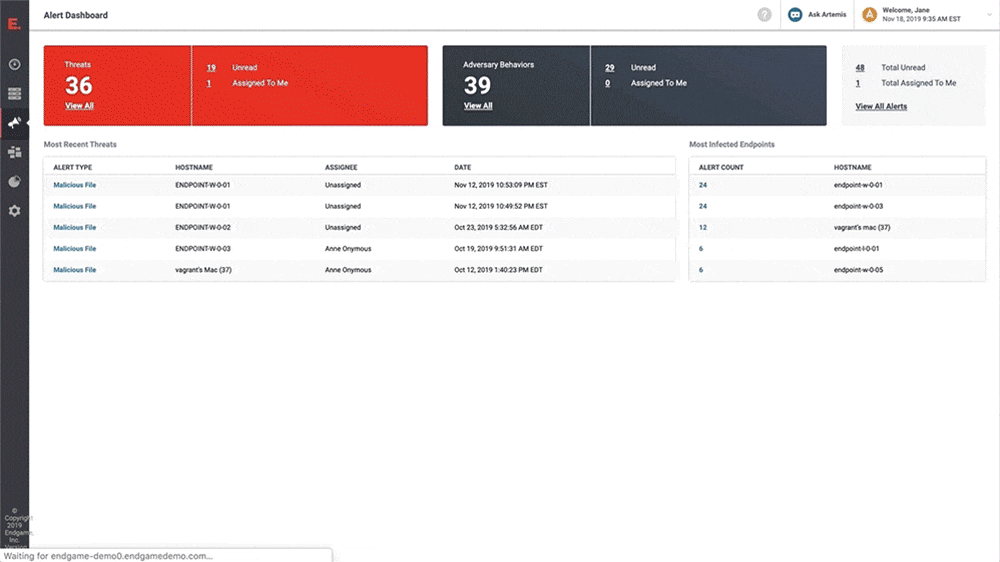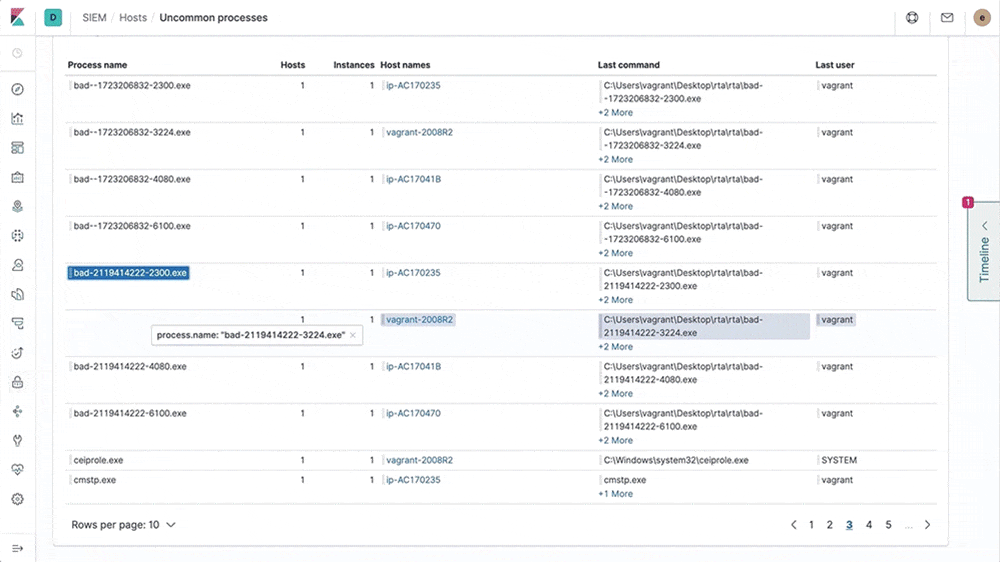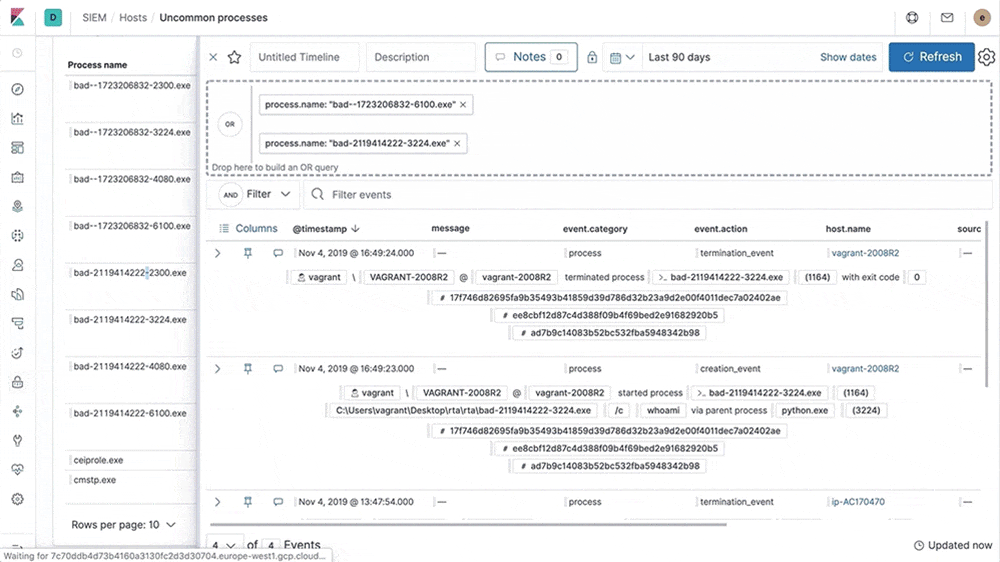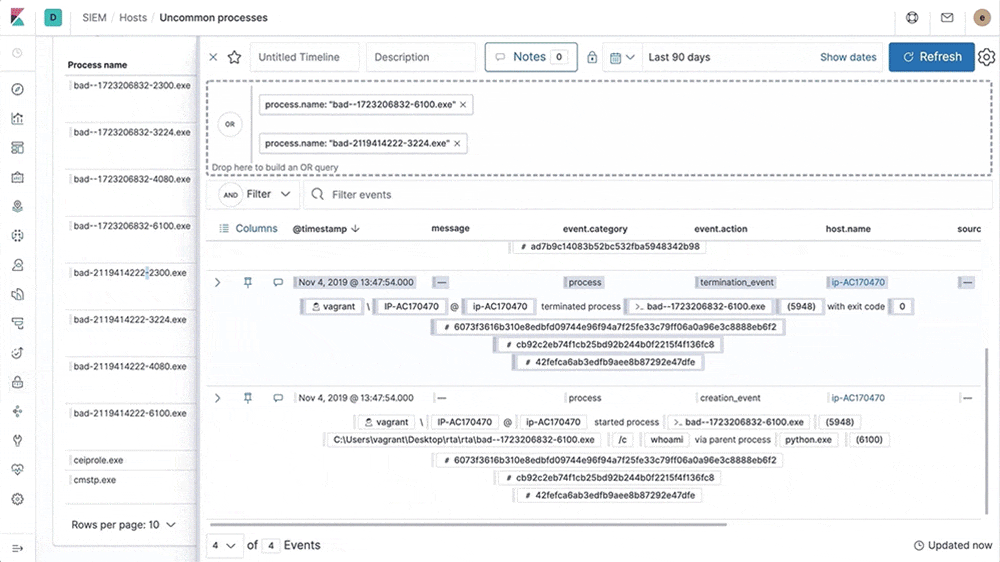
Visualize endpoint event data with a Kibana dashboard
With our latest update, users of the Elastic Stack now have a dedicated view into their streamed data from Elastic Endpoint Security. This view shows trends in the data being sent and provides actionable insights into the management of endpoint data, allowing security and operations analysts to better understand and manage their data.
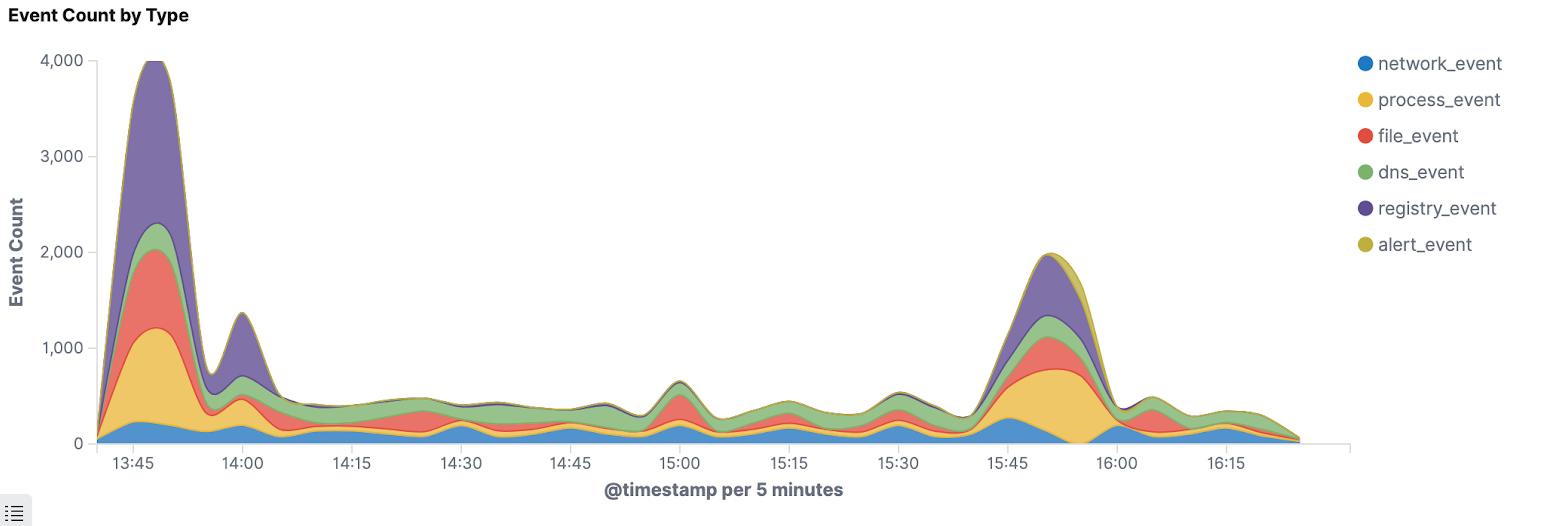
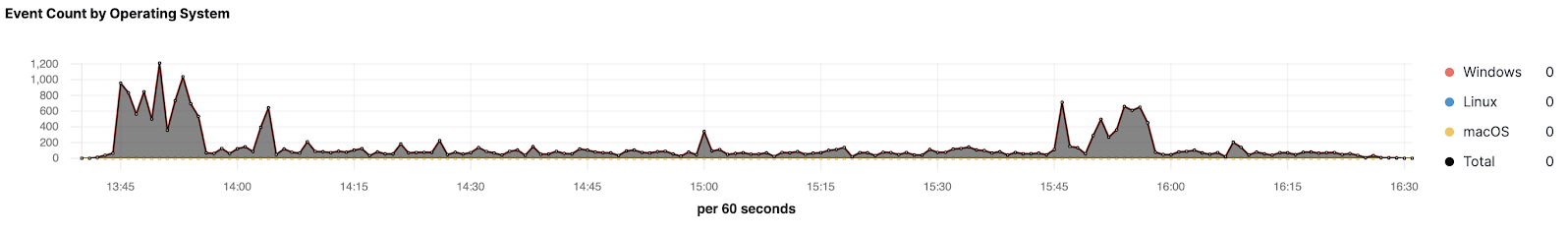
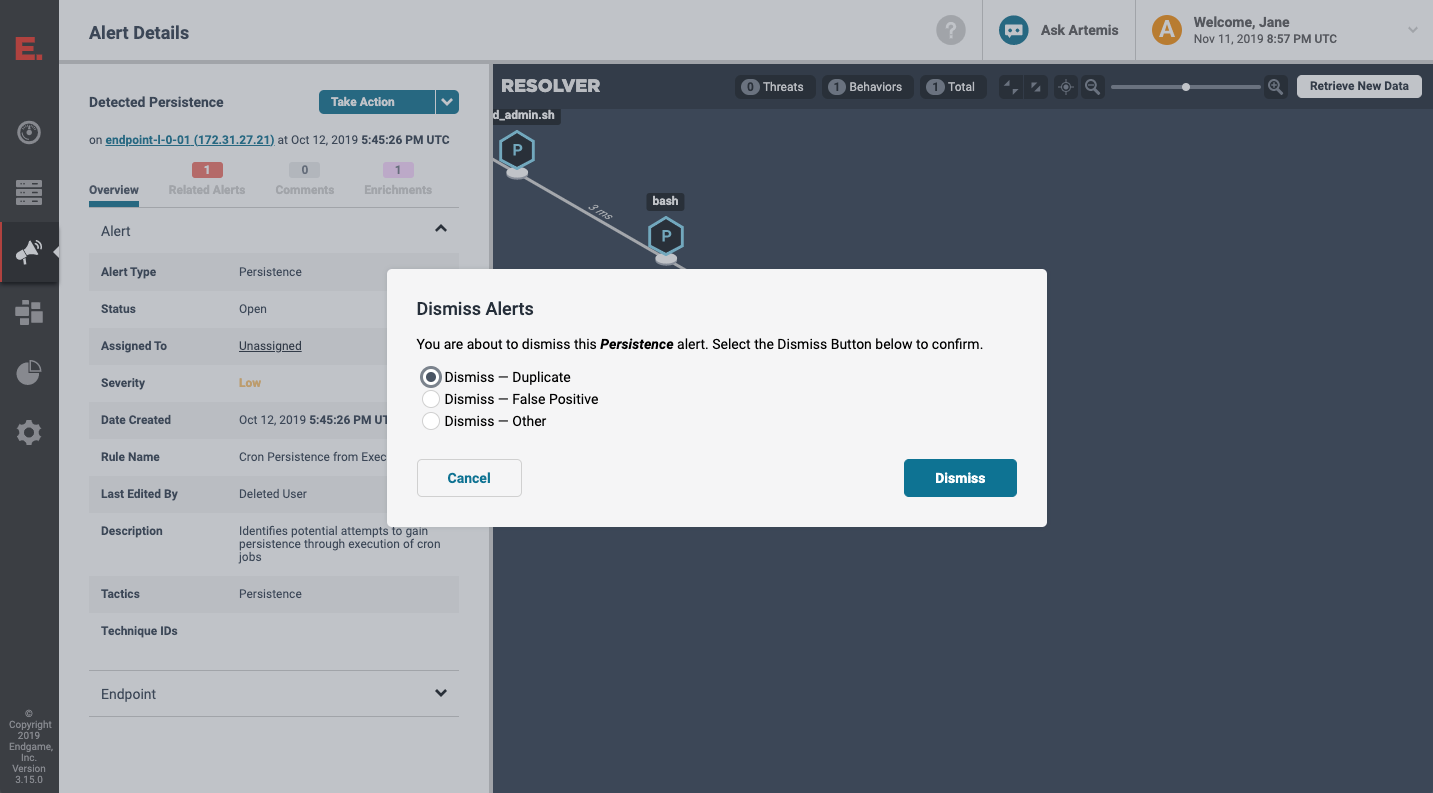
Provide reasons for dismissing alerts
Users of Elastic Endpoint Security can now select a specific reason for dismissing an alert. This feature adds to our existing set of collaboration and workflow tools. Users can dismiss an alert as a duplicate, a false positive, or dismiss it in an “other” state, which means security analysts can now share information and reasons for completing their work. They can also leverage our robust API to build their own actionable dashboards and collaborate with other analysts.
Get started today
Want to give Elastic SIEM a spin? Check out our latest version on Elasticsearch Service on Elastic Cloud or install the Elastic Stack.
Already have Elastic Common Schema (ECS) data in Elasticsearch? Just upgrade to 7.5 to try the latest version of Elastic SIEM.
To simplify your journey, this material can help you get started:
- Read about Elastic SIEM, try an Elastic SIEM demo, and review the Elastic SIEM documentation.
- Join us at an Elastic{ON} Tour stop to learn more about Elastic SIEM and Elastic Endpoint Security.